In any server environment, controlling who can access what is critical for security and stability. That’s where Role-Based Access Control (RBAC) comes in, a structured method to manage access based on user roles rather than individual permissions.
Let’s explore how RBAC works, why it matters, and how ServerAvatar simplifies RBAC for your servers.
What is RBAC?
Role-Based Access Control (RBAC) is a system for managing access to computer or server resources based on defined roles within an organization. Instead of manually assigning permissions to each user, administrators assign permissions to roles, and users are then added to those roles.
Think of it as giving employees different keys based on their jobs, one for finance, one for HR, and one for IT, rather than creating a unique key for each person.
Why RBAC Matters for Servers
Servers are the backbone of modern IT infrastructure. A small misconfiguration can lead to unauthorized access, data breaches, or accidental changes that bring down critical services. RBAC provides a structured way to control who can do what on a server, minimizing human error and improving security.
Core Components of RBAC
- Roles: Roles are essentially job titles or functions within your server environment. Examples include “Database Admin,” “Web Server Manager,” or “Read-Only User.” Each role represents a set of responsibilities and associated access rights.
- Permissions: Permissions define what actions a role can perform, such as read, write, execute, or delete files and system settings. Permissions are mapped to roles, ensuring that users can only perform tasks they’re authorized to do.
- Users and Groups: Users are the individuals accessing the server, while groups help organize users with similar responsibilities. In RBAC, you assign users to roles or groups to inherit permissions automatically.
Benefits of Using RBAC on Servers
- Enhanced Security: RBAC reduces the risk of unauthorized access by limiting what users can do. No one gets more permissions than necessary, keeping sensitive data safe.
- Simplified Management: Managing permissions individually for dozens or hundreds of users is a nightmare. RBAC centralizes control, making it easier to manage large server environments.
- Compliance and Audit Readiness: Many regulations, such as GDPR and HIPAA, require controlled access to sensitive data. RBAC makes auditing and demonstrating compliance straightforward.
How ServerAvatar Helps You Implement RBAC Effortlessly
ServerAvatar is a platform to simplify the hosting and management of servers and applications. It simplifies the process of deploying and managing PHP and Node.js based web applications on servers.
ServerAvatar makes managing servers and web applications simple, secure, and efficient. Instead of manually configuring users and permissions on every server, you can manage everything from a centralized dashboard using built-in RBAC capabilities.
ServerAvatar’s Organization Management system allows you to:
- Add team members.
- Assign roles and permissions.
- Monitor activities across all servers.
This eliminates the complexity of manual configuration and provides full visibility over your infrastructure.
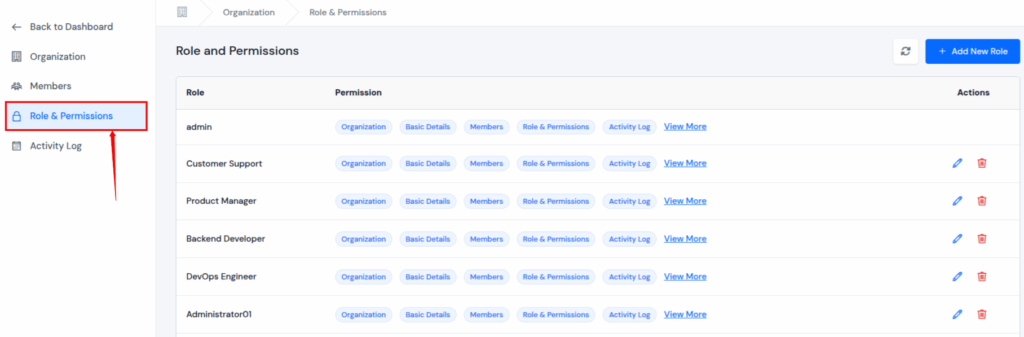
Role and Permission Management in ServerAvatar
ServerAvatar provides a dedicated Roles & Permissions system that allows fine-grained control over what each user can do.
- Create Custom Roles: Define roles like Server Manager, Developer, or Billing Admin.
- Assign Granular Permissions: Choose exactly which actions users can perform, from managing servers to viewing billing or modifying organization settings.
- Secure Collaboration: Share access safely with your team without giving full administrative control.
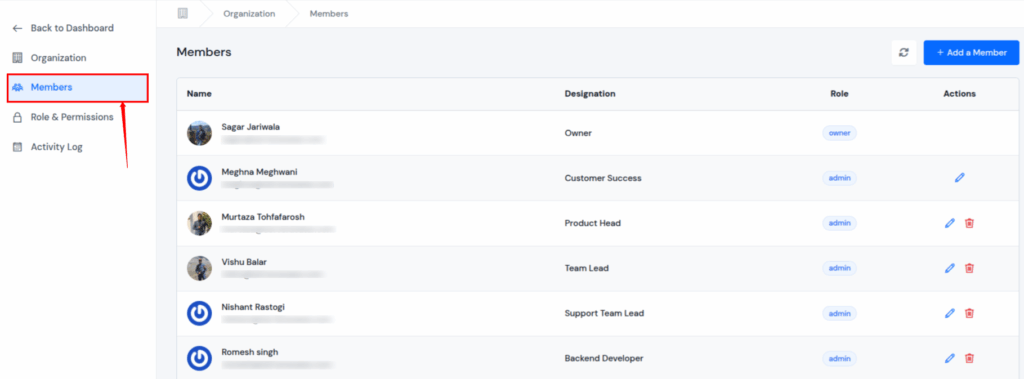
Manage Members and Teams Easily
In ServerAvatar, you can add members to your organization and assign them specific roles instantly. Each member’s permissions are managed by their assigned role, ensuring that no one can access what they shouldn’t.
- Invite multiple team members.
- Assign or revoke access with a few clicks.
- Maintain complete control over your organization’s structure.
Assign Specific Role and Permission to Members
With ServerAvatar, you can control what each team member can do by assigning them specific roles and permissions. This ensures that every user only has access to the actions and data necessary for their responsibilities, nothing more, nothing less.
With customizable roles, you can define permissions such as managing servers, viewing billing, or editing organization settings. This granular access control strengthens security and improves collaboration within your team.
- Create or edit custom roles with specific permissions.
- Assign roles to members based on their job functions or responsibilities.
- Update or revoke permissions anytime with just a few clicks.
- Enforce least-privilege access, minimizing the risk of unauthorized actions.
By assigning specific roles and permissions to your team members, ServerAvatar makes access management seamless, transparent, and secure across your entire organization.
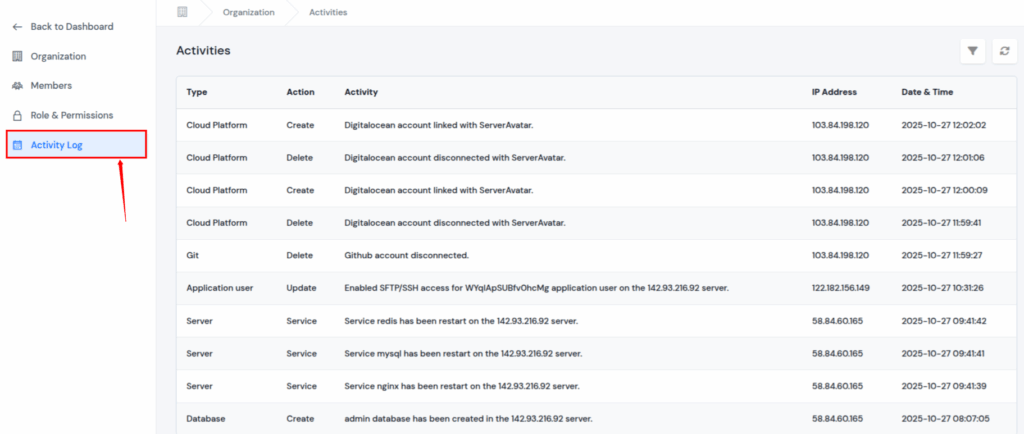
Monitor User Actions with Activity Logs
The Organization Activity page displays the history of all activities that have occurred within your organization. This includes activities such as creating new members, updating billing details, changing permissions, and more.
With Activity Logs, you can:
- Track every action.
- Identify every activity quickly.
- Filter and review logs easily, ensuring full visibility into your organization’s operations.
Key Features of ServerAvatar for RBAC and Server Security:
- User and Role Management: Easily create roles and assign specific permissions to users without manual configuration.
- Granular Permissions: Assign precise permissions to roles, ensuring users only access what they need.
- Centralized Dashboard: Manage all connected servers from a single interface, whether self-managed or on ServerAvatar infrastructure.
- Audit and Monitoring: Track user actions and server activity for security and compliance purposes.
- Secure Multi-Server Support: Apply RBAC policies consistently across unlimited servers with the Self-Managed Server add-on.
- Time-Saving Automation: Reduce administrative overhead with automated role assignments and permission updates.
With ServerAvatar, implementing RBAC on your servers is no longer a complex, technical headache; it’s simple, secure, and a few clicks away.

RBAC Implementation With ServerAvatar:
- Log in to your ServerAvatar account. Navigate to the “Team Management” section from the Dashboard.
You can explore all the mentioned Features in the Team Management section.
Setting Up RBAC on Linux Servers (Manually)
If you’re managing servers manually, Linux provides commands like chmod, chown, and usermod to define access levels.
You can:
- Create groups with:
groupadd- Add users to groups using
usermod -aG- Verify permissions using
ls -l and
su - usernameHowever, this approach can become complex when managing multiple servers or large teams; that’s where ServerAvatar offers a simpler alternative.
Common RBAC Challenges and How to Solve Them
| Challenge | Solution |
|---|---|
| Overlapping Roles | Consolidate roles or set role priorities. |
| Permission Sprawl | Review and audit permissions regularly. |
| Scaling Issues | Use centralized tools like ServerAvatar to automate RBAC. |
FAQs
Can RBAC be used on both Linux and Windows servers?
Yes. RBAC can be applied to both environments using built-in tools or management platforms like ServerAvatar.
How often should I review user roles and permissions?
It’s recommended to review them every 3–6 months or after organizational changes.
Can a single user have multiple roles in ServerAvatar?
Currently, each member has one assigned role per organization, but roles can include multiple permissions to cover necessary tasks.
What happens if a member leaves my organization?
You can instantly revoke access from the ServerAvatar dashboard, ensuring immediate security compliance.
How does ServerAvatar ensure activity transparency?
Every action, from server updates to role changes, is logged in the Activity Logs section for full traceability.
Stop Wasting Time on Servers. Start Building Instead.
You didn’t start your project to babysit servers. Let ServerAvatar handle deployment, monitoring, and backups — so you can focus on growth.
Deploy WordPress, Laravel, N8N, and more in minutes. No DevOps required. No command line. No stress.
Trusted by 10,000+ developers and growing.
