Keeping your server clean and secure is one of the most important parts of server management. When your system is exposed to the internet, it’s vulnerable to a variety of security threats, from malware infections to rootkits, trojans, and backdoors. One of the most effective ways to safeguard your server is by using reliable malware scanners like ClamAV.
In this guide, we’ll walk you through how to install, configure, and use ClamAV and other malware scanners on your server to keep it protected from malicious software. By the end, you’ll have a clear understanding of how to set up automated scans, monitor threats, and maintain a secure hosting environment.
What Is ClamAV?
ClamAV (Clam AntiVirus) is an open-source antivirus engine designed specifically for detecting malware, viruses, trojans, and other malicious threats on Linux-based servers. It’s lightweight, flexible, and highly effective for scanning files, directories, and emails, which makes it one of the most widely used antivirus tools in server environments.
Some of its key features include:
- Multi-format support: Detects a wide range of file types, including compressed archives and executable files.
- Automatic database updates: Keeps your virus definitions current.
- Command-line interface: Easy to automate and integrate into scripts.
- Email scanning: Perfect for mail servers to detect infected attachments.
Why You Should Use Malware Scanners on Your Server
Servers, especially those hosting websites, databases, or email services, are frequent targets for cyberattacks. Even a single infected file can compromise the entire system. Here are some major reasons to use a malware scanner like ClamAV:
- Early Threat Detection: Identify malware before it spreads or causes damage.
- Data Protection: Prevent data theft or corruption from malicious scripts.
- System Stability: Avoid performance drops caused by infected processes.
- Compliance: Meet security requirements for GDPR, HIPAA, or PCI DSS.
- Email Security: Stop malicious attachments and phishing attempts at the source.
In short, malware scanners are your first line of defense in maintaining a healthy and secure server environment.
Installing ClamAV on Linux Servers
ClamAV is available in most Linux distributions’ repositories, so installation is straightforward. Below are the installation commands for popular distros:
For Ubuntu/Debian:
sudo apt update
sudo apt install clamav clamav-daemon -yFor CentOS/RHEL:
sudo yum install epel-release -y
sudo yum install clamav clamav-update -yFor Fedora:
sudo dnf install clamav clamav-update -yOnce installed, you can verify the installation using:
clamscan --version
This will display the ClamAV version and confirm it’s ready for use.
Updating the ClamAV Database
ClamAV relies on its virus definition database to detect known threats. Keeping this database updated is crucial for accurate detection.
To update the database manually, run:
sudo freshclamTo automate the process, ensure the ClamAV daemon or freshclam service is enabled:
sudo systemctl enable clamav-freshclam
sudo systemctl start clamav-freshclamThis will keep your malware signatures up to date automatically.
How to Scan Files and Directories with ClamAV
Once ClamAV is installed and updated, you can begin scanning your server. The clamscan command is used for this purpose.
Basic Scan:
clamscan /path/to/directoryScan with Detailed Output:
clamscan -r -i /home- -r enables recursive scanning (scans subdirectories).
- -i shows only infected files.
Move or Delete Infected Files Automatically:
clamscan -r --remove /var/wwwNote:- Be careful with the –remove option, it permanently deletes infected files. It’s safer to quarantine them first.
Quarantine Infected Files:
clamscan -r --move=/quarantine /homeThis moves infected files to a specified quarantine directory for manual inspection.
Automating Scans with ClamAV Daemon (clamd)
ClamAV comes with a daemon service (clamd) that allows you to run scans faster by keeping the engine loaded in memory. This is perfect for real-time or scheduled scanning.
Enable and start clamd:
sudo systemctl enable clamav-daemon
sudo systemctl start clamav-daemonOnce running, you can integrate it with other services, like a mail server or cron job, for automated scanning.
Setting Up Scheduled Scans (Cron Jobs)
You can automate malware scans using cron jobs, ensuring regular system checks without manual effort.
- Open the cron table:
- sudo crontab -e
- Add a daily scan entry (example):
- 0 2 * * * clamscan -r /home –log=/var/log/clamav/daily-scan.log
This example runs a full scan every day at 2 AM and logs the output.
Checking and Reading Scan Logs
By default, ClamAV records scan results in the system logs. You can view them at:
cat /var/log/clamav/clamav.logYou can also specify a custom log path using the –log flag during scans.
Reviewing logs regularly helps identify potential threats early and verify that scans are running successfully.
Scheduled CronJobs With ServerAvatar:
ServerAvatar is a platform to simplify the hosting and management of servers and applications. It simplifies the process of deploying and managing PHP and Node.js based web applications on servers. Here are some of the key features of ServerAvatar:
- One-Click App Deployment
- Managed and Self-Managed Server Options
- Scalable Infrastructure (resources) with managed server
- Automatic Free SSL Certificates
- Built-in File Manager and Server Monitoring
- Automated Backups
- Team Management
- Cron Job Management
- Automatic Security Updates
- Built-in security features like firewall, fail2ban, etc.
- Log Monitoring Suite (InsightHub)
- WhiteLabel and Reseller Panel
- 24/7 Support from an expert team
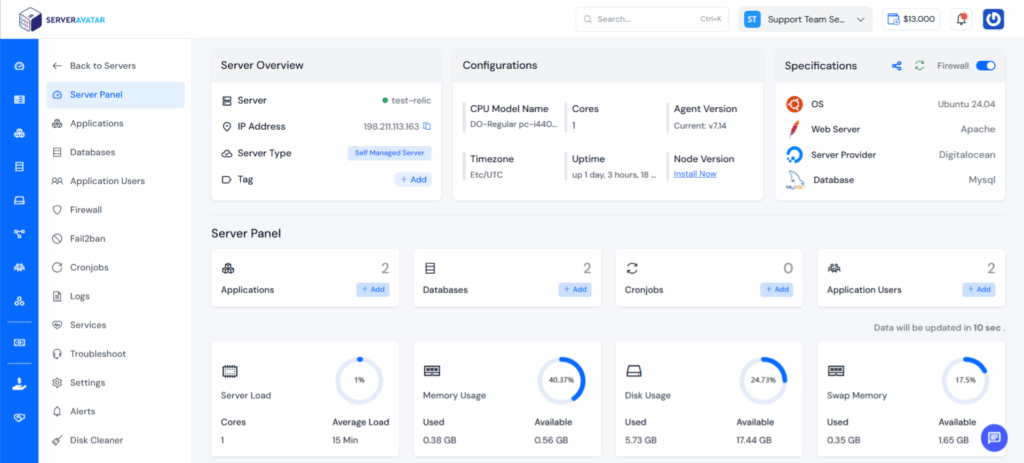
If you’re using ServerAvatar to manage your servers and applications, you can easily set up the Cron Jobs for Scheduled Scans by navigating to Cronjobs section from server panel.
- Login to ServerAvatar, and click on the Server Dashboard icon from Dashboard section.
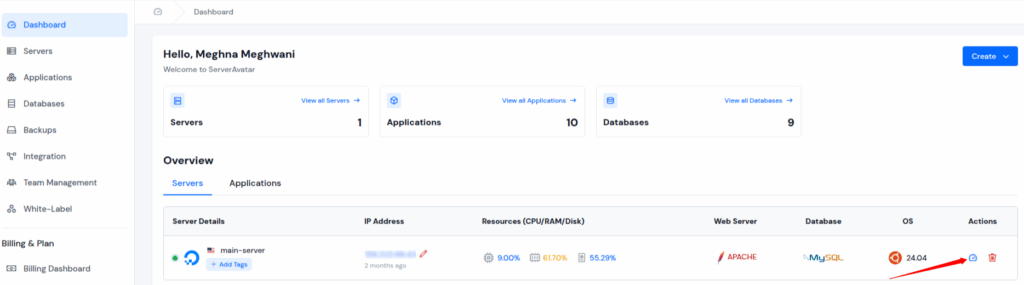
- Navigate to the Cronjobs section from the left hand sidebar, and click on ‘Create a Cronjob‘ button.
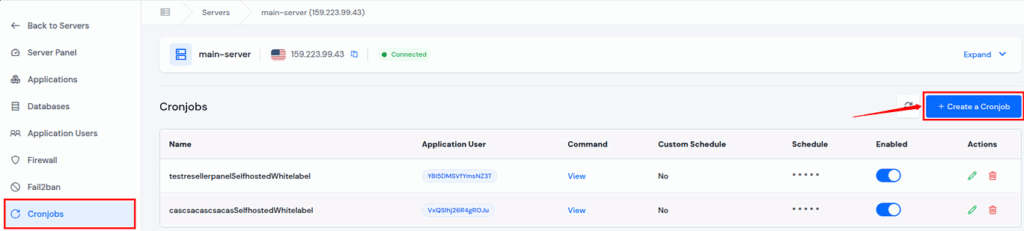
- Fill up the details such as Name, Application User, Command to execute, and Schedule time for Cronjobs, and click on ‘Create a Cronjob‘ button.
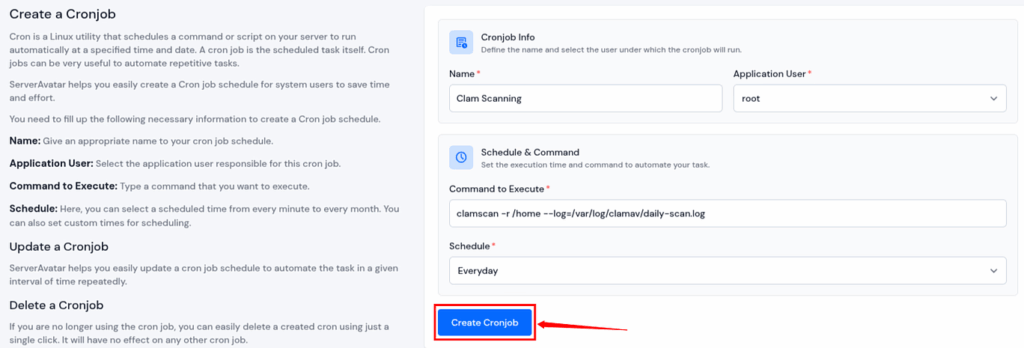
- Additionally, you can set cronjobs at your preferred time by selecting the custom option in the ‘Schedule’ field.
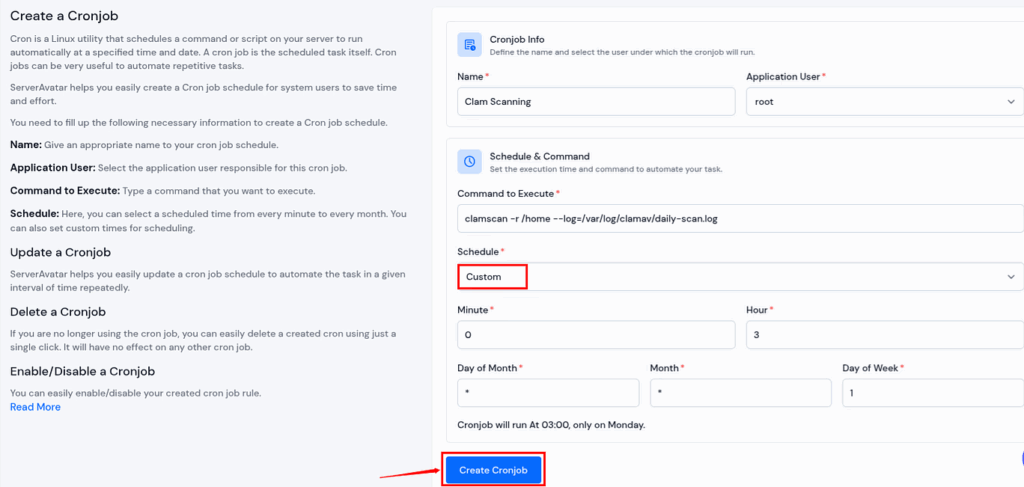
- For example, as shown in the image above, (0 3 * * 1), this will run every Monday at 3:00 AM
- Explanation,
┌──────── minute (0 – 59)
│ ┌────── hour (0 – 23)
│ │ ┌──── day of month (1 – 31)
│ │ │ ┌── month (1 – 12)
│ │ │ │ ┌ day of week (0 – 7) (Sunday = 0 or 7)
│ │ │ │ │
0 3 * * 1 → every Monday at 3:00 AM
- Creating a Cron Job with ServerAvatar is quick and straightforward.

Alternative Malware Scanners You Can Use
While ClamAV is one of the best free tools, you can pair or compare it with other malware scanners for added protection.
1. Maldet (Linux Malware Detect)
- Designed for web servers.
- Integrates with ClamAV for enhanced detection.
- Ideal for scanning website files on shared hosting servers.
2. Rkhunter
- Detects rootkits, backdoors, and local exploits.
- Excellent for security auditing.
3. Sophos Antivirus for Linux
- Offers real-time scanning and centralized management.
- Suitable for enterprise environments.
4. Bitdefender GravityZone
- Enterprise-grade security suite with Linux support.
- Provides cloud-based malware analysis.
Using a combination of these tools can offer layered protection against different types of threats.
Best Practices for Using ClamAV and Malware Scanners
To maximize protection, follow these best security practices:
- Keep ClamAV and system packages updated.
- Run scheduled scans at off-peak hours to avoid slowing down performance.
- Regularly review scan logs for suspicious activity.
- Quarantine before deleting infected files to avoid accidental data loss.
- Combine ClamAV with other tools like Rkhunter or Maldet for deeper scans.
- Secure server configurations (firewalls, SSH keys, limited root access).
By combining good scanning habits with strong security practices, you can significantly reduce your server’s risk of infection.
Troubleshooting Common ClamAV Issues
If you run into errors while using ClamAV, here are quick fixes:
- FreshClam Fails to Update:
Try running sudo freshclam –verbose to view detailed errors.
Check if your system time and DNS are correctly configured. - Permission Denied Errors:
Run ClamAV as root or use sudo.
Ensure the scanning user has permission to access all directories. - High CPU Usage:
Schedule scans during low-traffic hours.
Use nice or ionice to lower ClamAV’s priority.
Frequently Asked Questions
1. Is ClamAV free to use?
Yes, ClamAV is completely free and open-source. You can use it on personal or commercial Linux servers without any licensing fees.
2. Does ClamAV provide real-time protection?
By default, ClamAV doesn’t offer real-time protection. However, you can enable real-time scanning by using ClamAV Daemon (clamd) or integrating it with third-party tools that monitor files in real-time.
3. How often should I run malware scans on my server?
It’s best to schedule daily or weekly scans, depending on how frequently your files change. Automated cron jobs are ideal for maintaining consistent scan routines.
4. Can ClamAV remove infected files automatically?
Yes, ClamAV can delete or move infected files automatically using the –remove or –move flags. However, it’s safer to quarantine files first to avoid accidental data loss.
5. Can I use ClamAV with ServerAvatar?
Yes! If you manage your servers using ServerAvatar, you can easily set up cron jobs for automated malware scans, no manual configuration required.
Conclusion
Keeping your server free from malware isn’t just a security measure, it’s an essential part of maintaining performance, reliability, and trust. Tools like ClamAV provide a powerful, open-source solution for detecting and eliminating viruses, trojans, and other malicious threats before they cause harm.
When combined with automated scans, regular updates, and proper system monitoring, ClamAV can help you build a robust security foundation for your Linux servers. And if you’re using ServerAvatar, setting up automated cron jobs and managing scans becomes even easier, saving you time while ensuring your servers remain clean and secure.
By taking a proactive approach to malware detection and following the best practices outlined above, you can protect your applications, data, and users from potential threats with confidence.
