When running PHP on a server, security is everything. You don’t want your application, or anyone else’s, accessing sensitive files outside of its intended directory. That’s where open_basedir comes in. It’s a powerful but often misunderstood PHP directive that can significantly tighten the security of your PHP environment.
In this blog, we’ll break down what open_basedir is, why it matters, and most importantly, how to configure it properly step by step. Whether you’re running a shared hosting environment or managing your own server with a platform like ServerAvatar, this guide will help you stay secure and in control.
What is open_basedir in PHP?
The open_basedir directive is a PHP configuration setting that restricts the PHP scripts to access only certain directories on the file system. In other words, it prevents scripts from snooping around in other parts of the server’s directory tree.
When set, PHP will refuse to open any file outside of the defined path(s), even if your script tries to.
Why is open_basedir Important for Security?
PHP has powerful file-handling functions like fopen(), file_get_contents(), and require_once(), which can access files anywhere on the server. Without restrictions, a misconfigured or vulnerable script could expose confidential files like /etc/passwd, .env files, or private server keys.
By using open_basedir, you ensure:
- File access is limited only to necessary directories
- Cross-site scripting (XSS) attacks and file traversal vulnerabilities are minimized
- Your multi-user or multi-site environments remain isolated
If you’re using ServerAvatar, you’ll be glad to know that it allows easy configuration of PHP directives like open_basedir directly from the control panel for each web app or domain. This makes it super simple to apply directory-level security without diving into the terminal.
How Does open_basedir Work?
Once open_basedir is enabled, PHP checks all file operations like reading, writing, or including a file. If the file path falls outside of the allowed directory, the script fails and throws a warning or error.
Example:
If your open_basedir is set to:
open_basedir = /var/www/html/Then trying to access:
file_get_contents('/etc/passwd');result in:
Warning: file_get_contents(): open_basedir restriction in effect. File(/etc/passwd) is not within the allowed path(s)Where Can You Set open_basedir?
You can configure open_basedir in multiple places depending on your server setup:
- ServerAvatar Panel – Simplified per-app configuration (Recommended)
- php.ini – Global setting (server-wide)
- .htaccess – Apache per-directory config
- httpd.conf or vhost config – Apache/Nginx virtual hosts
Let’s break these down with steps.
Step-by-Step: How to Configure open_basedir Securely
Identify Allowed Directories
Determine which directories your PHP app needs to access. For example:
- Web root: /var/www/myapp/
- Temporary folder: /tmp/ (often required for sessions or uploads)
Important: If you forget to allow /tmp/, PHP sessions or file uploads may break.
Method 1: Set via ServerAvatar (Easiest Method)
What is ServerAvatar
ServerAvatar is a cloud server management platform that makes it easy to host websites and applications. It lets you manage servers, deploy apps like WordPress or Laravel, and handle backups, SSL, monitoring, and more—all through a user-friendly dashboard, without needing deep server knowledge.
If you’re using ServerAvatar, here’s how you do it:
- Log in to ServerAvatar Panel
- Go to Your Server, then Navigate Your Application
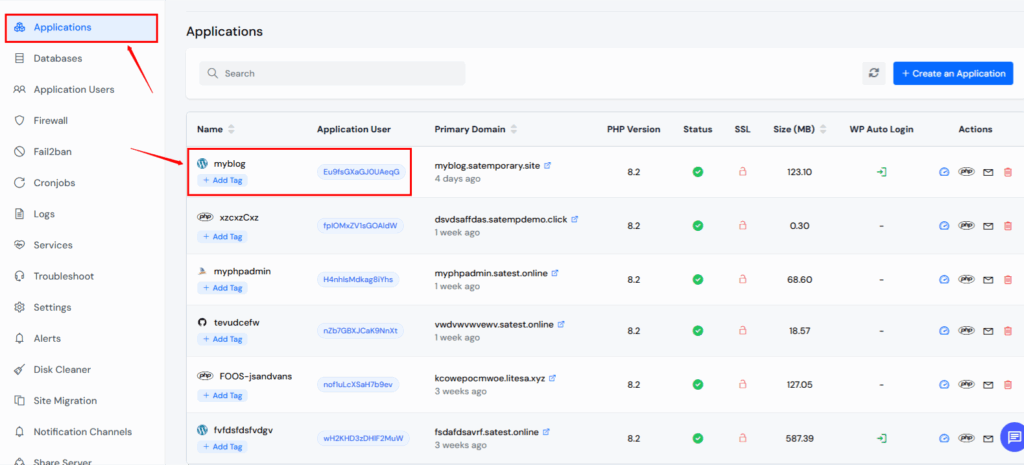
Under open_basedir, add the allowed paths (e.g. /home/Eu9fsGXaGJ0UAeqG/myblog:/var/lib/php/sessions:/tmp:)
this is my application path your path would be different.
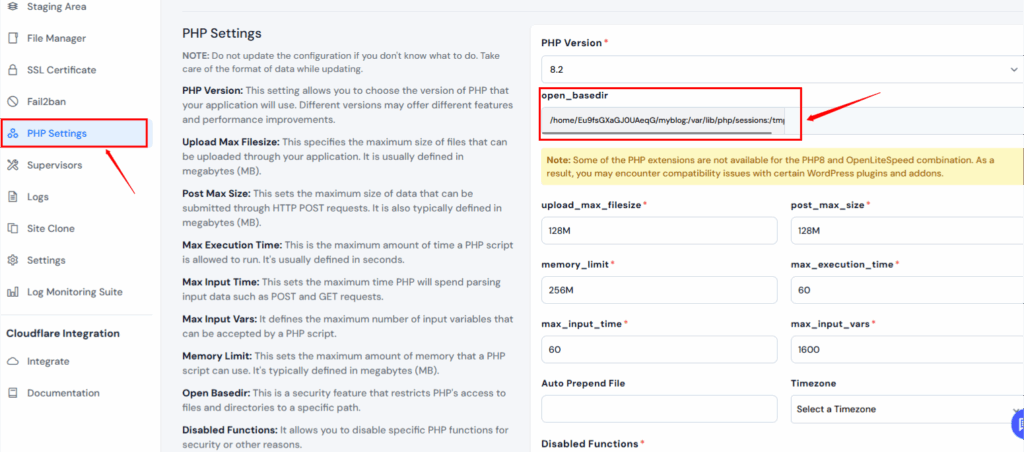
- Click on update settings
- ServerAvatar will automatically apply changes and restart the necessary services
This is the easiest and safest way for users who don’t want to mess with server files manually.
Method 2: Set in php.ini (Global Method)
Find Your PHP Config File
Run this command to find where PHP is reading settings from:
php --iniYou’ll see something like:
Loaded Configuration File => /etc/php/8.2/apache2/php.iniThat’s the file we need to edit.
Open the File to Edit
Use a command-line editor like nano:
If using Apache:
sudo nano /etc/php/8.2/apache2/php.iniIf using PHP-FPM:
sudo nano /etc/php/8.2/fpm/php.iniAdd the open_basedir Setting
Inside the file, scroll down or search (Ctrl + W) for:
open_basedirIf it’s not there, add this line anywhere (preferably near the other file-related settings):
open_basedir = "/var/www/myapp/:/tmp/"Save and Exit
In nano:
- Press Ctrl + O → Save
- Press Enter → Confirm
- Press Ctrl + X → Exit
Restart the Web Server
To make the changes take effect, restart your web server.
If you use Apache:
sudo systemctl restart apache2If you use PHP-FPM:
sudo systemctl restart php8.2-fpmYou’re Done!
Now PHP can only access files in:
- /var/www/myapp/
- /tmp/
If it tries to access anything else (like /etc/passwd), it will fail with an error — this is good for security!
Method 3: Set in .htaccess (Apache Only)
This method is for you if you don’t have access to php.ini, but your server uses Apache with mod_php (not PHP-FPM).
Step-by-step:
Go to your website folder:
Example:
/var/www/myapp/Open or create the .htaccess file:
sudo nano /var/www/myapp/.htaccess\Add this line inside the file:
php_value open_basedir "/var/www/myapp/:/tmp/"Save and exit:
- Ctrl + O to save
- Enter to confirm
- Ctrl + X to exit
Restart Apache:
sudo systemctl restart apache2Works only if PHP runs as Apache module
Does not work with PHP-FPM

Method 4: Set in Virtual Host (Apache or Nginx)
Open your virtual host config file (usually in /etc/apache2/sites-available/):
sudo nano /etc/apache2/sites-available/myapp.confAdd this inside the <VirtualHost> block:
apache
<Directory "/var/www/myapp">
php_admin_value open_basedir "/var/www/myapp/:/tmp/"
</Directory>Save and exit
Restart Apache:
sudo systemctl restart apache2B) For Nginx (with PHP-FPM)
Open the PHP-FPM pool config file (usually in /etc/php/8.2/fpm/pool.d/www.conf or a custom pool):
sudo nano /etc/php/8.2/fpm/pool.d/www.confAdd this line at the bottom:
php_admin_value[open_basedir] = /var/www/myapp/:/tmp/Save and exit
Restart PHP-FPM:
sudo systemctl restart php8.2-fpmDone!
Now PHP will only be allowed to access files in:
- /var/www/myapp/
- /tmp/
Trying to access anything else will result in a permission error, which increases security.
Let me know if you need help checking whether your server uses Apache module or PHP-FPM!
Common Mistakes to Avoid
- Forgetting /tmp/ – This will break uploads, caching, or sessions.
- Misspelling the paths – PHP won’t correct invalid paths.
- Setting it too broadly – Avoid using / as that defeats the whole purpose.
- Relying on ini_set() – Many hosts disable changing open_basedir at runtime.
How to Test if open_basedir is Working
Create a quick test script:
<?php
echo file_get_contents('/etc/passwd');
?>If you’ve configured open_basedir correctly, you should see a PHP warning instead of the file contents. That’s good!
You can also run:
phpinfo();And check the Local Value and Master Value for open_basedir.
Real-World Use Case: Multi-Site Hosting
Let’s say you’re hosting multiple client websites on the same server:
- /var/www/site1
- /var/www/site2
By setting:
open_basedir = /var/www/site1/:/tmp/for site1
open_basedir = /var/www/site2/:/tmp/for site2, you’re making sure one site can’t access files from another.
Platforms like ServerAvatar automate this for each website you add, ensuring isolation and security by default.
Best Practices for open_basedir Configuration
- Always include /tmp/
- Use absolute paths
- Isolate each site’s directory
- Use ServerAvatar for simplified per-site settings
- Check logs after enabling – Fix errors if scripts can’t access valid files
- Combine with other PHP restrictions like disable_functions for maximum protection
Frequently Asked Questions (FAQ)
What is open_basedir in PHP?
open_basedir is a PHP configuration directive that limits the files a PHP script can access to a specific directory or set of directories. It helps prevent unauthorized access to sensitive files outside of the intended folders.
Why should I use open_basedir?
Using open_basedir improves your server’s security by restricting PHP scripts to specific directories. This is especially important in shared hosting or multi-site environments where one site could otherwise access another site’s files.
Can I set multiple directories in open_basedir?
Yes, you can specify multiple directories by separating them with a colon (:) on Linux or a semicolon (;) on Windows.
ini open_basedir = /var/www/myapp/:/tmp/
What happens if a script tries to access a file outside the allowed directory?
PHP will throw a warning or error, and the script will not be able to read or write the file.
Example error:
css Warning: file_get_contents(): open_basedir restriction in effect…
Is open_basedir enough for complete PHP security?
- No, it’s just one part of the puzzle. For complete PHP security, you should also:
- Disable dangerous functions (disable_functions)
- Set proper file/folder permissions
- Use secure coding practices
- Keep your PHP version updated
Conclusion
To sum up, open_basedir is one of PHP’s most underrated but powerful security features. Whether you’re running one site or managing a fleet of them, it acts like an invisible fence around your application’s file access.
By configuring it properly:
- You minimize risk
- You prevent unauthorized file access
- And you enhance isolation in multi-site environments
If you’re using ServerAvatar, this becomes even easier—no manual configs, just a few clicks. For self-managed environments, follow the steps above and always test after applying.
Stay safe. Keep your PHP secure. And don’t let your scripts wander where they shouldn’t.
If you found this guide helpful, feel free to share or bookmark it for later.
