Imagine, you built your perfect house, but you neglected to lock the back door. From the front, it looks safe, but if you make one small error, intruders could get in. That’s how PHP security works, exactly. Your website may appear great on the outside, but if some PHP functions are still active, you’re almost asking hackers to get in.
PHP is a powerful and flexible language, but it has a lot of built-in functions that might be dangerous if you don’t utilise them correctly. When you turn them off, it’s like closing all the doors and windows in your digital home.
Let’s talk about the PHP features you should turn off for greater security and why this is a vital step for every server admin or website owner, even if you’re not a techie.
Why It is Important to Disable Some PHP Functions
When we create a blog or an online store, most of us don’t think about PHPgate PHP functions. But here’s the thing: some PHP functions are like letting somebody you don’t know into your house. They can run code, allow access to the system shell, and let files from other systems be incorporated.
When hackers gain their hands on these capabilities, they can utilise them to attack.
How hackers use PHP functions for advantage
Have you ever heard of backdoors or malware that gets into your computer? A lot of these attacks use PHP functions that are very risky. For instance, a hacker could submit a script that utilises “exec()” to conduct harmful commands. Or they may run concealed code with “eval().”
Real-world example? Uploading a shell script and using “system()” to take over the server is a typical attack. Turning off these features seals that door tightly.
How to Disable PHP Functions
The “php.ini” file is main PHP configuration file. You can turn off PHP functionalities at the server level by modifying this file. You can also set them up using “.htaccess” or the control panel itself, such as ServerAvatar, without having to use the command line or deal with technical issues.
No matter where you do it, the purpose is still the same: to prevent functions that could be exploited.
Let’s check out the different methods mentioned below to disable the PHP Functions:
Method 1: Using ServerAvatar
ServerAvatar is a platform to simplify the deployment and management of servers and applications. It simplifies the process of deploying and managing PHP and Node.js based web applications on servers. If you’re using ServerAvatar to manage your servers and applications, increasing the “upload_max_filesize” in PHP for your application is incredibly simple and doesn’t require editing PHP configuration files manually. ServerAvatar provides PHP configuration settings on application level for each application.
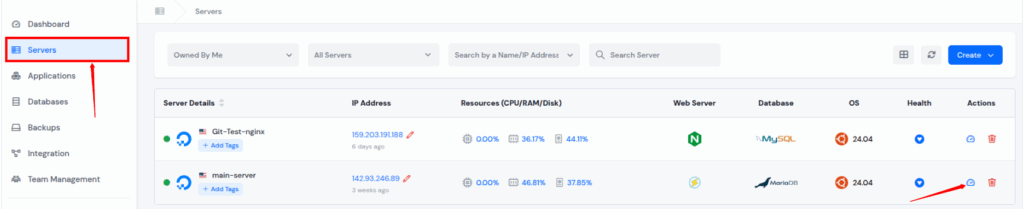
Step 1: Access ServerAvatar Panel
Log in to your ServerAvatar account and navigate to the Server panel by clicking on the Dashboard icon for the server where your application is hosted.
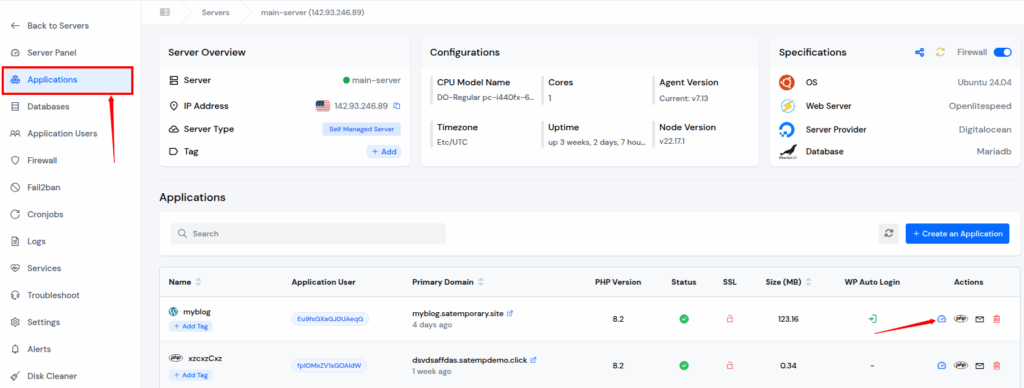
Step 2: Access Application Panel
Click on the application dashboard icon for the application you wish to turn off the “PHP Functions” in the Applications section of the left-hand sidebar..
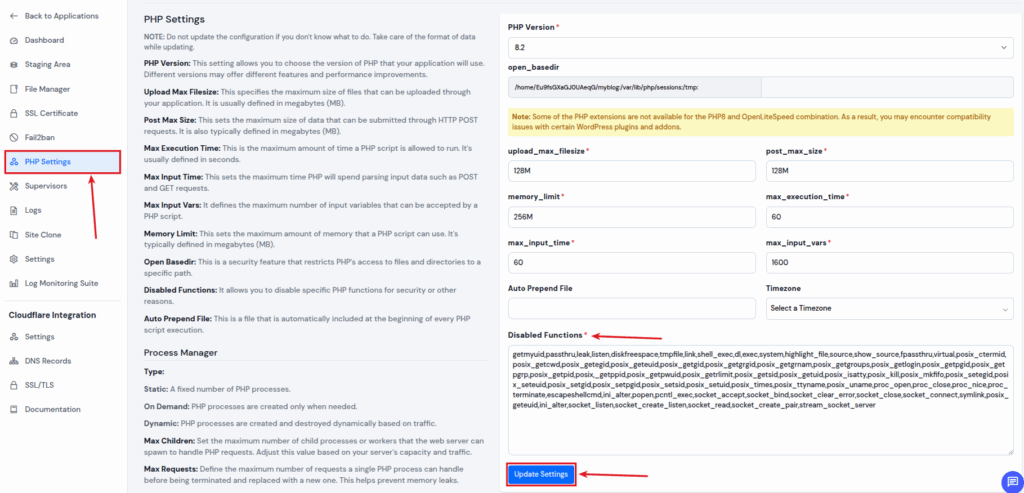
Step 3: Modify PHP Settings
On the left side of the application window, click on “PHP Settings.” You can change a number of settings under the PHP Settings area.
Find the field named Disabled Functions. It allows you to disable specific PHP functions for security or other reasons. You can check out all the PHP Disabled Functions mentioned in the field. You can enter or remove your desired function there, and click on “Update Settings” button at the bottom of the section.
ServerAvatar will automatically update the PHP configuration, and the change takes effect immediately. This method is very easy and ideal for beginners or anyone who wants a fast, error-free way to manage PHP settings without touching the command line.
Method 2: Editing the php.ini File
Step 1: Locate your php.ini file
Follow these steps to go to your php.ini file:
- For Apache, it is located at:
/etc/php/8.x/apache2/php.ini- “8.x” is the version of PHP, it should be different in your case. Replace 8.x with your actual PHP version (like 8.1, 8.2, etc.).
- For Nginx, it is located at:
/etc/php/8.x/fpm/php.ini- “8.x” is the version of PHP, it should be different in your case. Replace 8.x with your actual PHP version (like 8.1, 8.2, etc.).
Step 2: Disable PHP Functions
Find the “disable_functions” section in your “php.ini” file, and add the functions you want to disable. separate the functions by commas, as you can see in the image below.
Example:
disable_functions = exec, shell_exec, system, passthru, popen, proc_open, eval, assertRestart your web server afterward to apply changes.
- For Apache, it is located at:
sudo systemctl restart apache2- For Nginx, it is located at:
sudo systemctl restart nginxTop PHP Functions You Should Disable
Let’s break down the most dangerous PHP functions, what they do, and why you should consider disabling them.
1. exec()
Why it’s dangerous:
This function runs commands on the system. People often use it in assaults to open remote shells or download viruses.
Disable if you don’t have a good reason to perform system-level commands from your PHP scripts.
2. shell_exec()
Why it’s dangerous:
It does the same thing as exec(), except it gives you the whole output. Hackers enjoy this because it lets them access the contents of directories, get information about servers, or run whole scripts.
Disable because it gives you complete access to your shell, which is all you need to know.
3. system()
Why it’s dangerous:
Another function that runs commands at the system level. It’s like exec(), but it sends output straight to the browser.
Hackers use it to run bad commands and watch what happens right away.
4. passthru()
Why it’s dangerous:
You utilise this one to run system commands and provide raw output right away. People usually use it to run binary files.
Disable it to stop hackers from using server resources.
5. popen() and proc_open()
Why it’s dangerous:
Why they are dangerous:
Both functions provide you a lot of control over how processes execute. Attackers use them to make malware that stays on your computer and runs in the background.
If you’re not making a special app that needs them, block them.
6. eval()
Why it’s dangerous:
eval() runs a string as PHP code. People often call it the “nuclear bomb of PHP” because it can do anything if you use it wrong.
Used to mask and run code injections, which is common in malware. Turn this off unless you’re very sure you need it.
7. assert()
Why it could be dangerous:
In some cases, it can work like eval(). If you give it human input, your server is done for.
Best practice: Disable or switch to safer options.
8. base64_decode() (In Specific Cases)
Why it’s risky:
Not dangerous alone, but often used in malware to hide malicious payloads in encoded strings.
Caution:
If you’re not using it for legitimate decoding, consider blocking or monitoring its usage.
9. allow_url_fopen and allow_url_include
Why they’re risky:
They allow file functions to access URLs. This means someone could include remote malicious scripts into your application.
Disable by:
Setting these directives to Off in your php.ini file.
10. phpinfo()
Why it’s risky:
It shows detailed server information, PHP version, server paths, loaded modules. Useful for you, but also for hackers.
Pro tip:
Use it only in development and disable it on production servers.

Tips to Test After Disabling Functions
After disabling functions, test your site carefully. Some themes, plugins, or scripts may depend on them. Use logs and debugging tools to spot errors and identify any broken features.
Balance Between Functionality and Security
Security is essential, but you don’t want to break your website either. That’s where balance comes in. If you’re not using these risky functions, disable them. But always test thoroughly.
Analogy time: Think of these functions like sharp knives in your kitchen. Handy, but you wouldn’t leave them lying around if kids (aka hackers) could reach them.
Common Mistakes to Avoid
- Blindly disabling all functions without testing.
- Ignoring error logs after changes.
- Leaving phpinfo() active in production.
- Assuming plugins are safe, some rely on risky functions.
- Not restarting the server after updating php.ini.
FAQs
1. What is the best way to disable PHP functions?
Edit your php.ini file and add the risky functions to the disable_functions directive. Restart your server to apply changes.
2. Will disabling functions break my site?
It might, if your code or plugins depend on those functions. First, test always in staging environment.
3. Is eval() really that dangerous?
Yes. eval() can execute any PHP code from a string, including malicious input. It’s widely abused in attacks.
4. Can I disable functions in shared hosting?
Sometimes. If you don’t have access to php.ini, try using .htaccess or contact your hosting provider.
5. Should I disable functions if I use WordPress?
Yes, especially if you don’t need them. WordPress core doesn’t rely on most of these dangerous functions.
Conclusion:
Securing your PHP environment isn’t just a task for developers, it’s a responsibility for anyone managing a website or server. Leaving dangerous PHP functions enabled is like handing the keys of your server to an attacker. While PHP offers powerful tools, not all of them are meant to be left unlocked.
When it comes to securing your PHP-based websites, disabling high-risk functions is a smart and proactive step. You don’t need to be a cybersecurity expert to lock down your server, just a little knowledge and caution go a long way.
By disabling risky functions like exec(), shell_exec(), eval(), and others, you’re significantly reducing your website’s attack surface. Whether you do it manually via php.ini or use a user-friendly platform like ServerAvatar, the key is to act before a vulnerability is exploited.
Always remember that safety is about stopping things before they happen. Hackers are continually trying to get in. Don’t leave the door open.
