In today’s digital world, where servers are constantly exposed to threats, securing your Linux server is not optional, it’s essential. Whether you run a personal website, an enterprise app, or a cloud-based service, your Linux server is a target for hackers, malware, and automated bots. That’s where Linux server hardening comes in.
But what exactly is it? Let’s dive deeper.
Understanding Linux Server Hardening
What Is Server Hardening?
Server hardening means protecting your Linux server by reducing its vulnerability surface. It’s like locking every door and window of your house before you go on vacation. You remove unnecessary services, close open ports, and implement security best practices to ensure your server stays safe from intruders.
Why It Matters?
Even though Linux is considered more secure than many other operating systems, it’s not immune to attacks. Poor configurations, outdated software, or weak passwords can make your server an easy target.
Common Threats:
1. Brute-force login attempts:
- A brute-force attack occurs when an attacker uses automated scripts to repeatedly try different username and password combinations to gain access to an account or system. These attacks are typically launched using bots that can attempt thousands of login combinations per minute.
- If successful, attackers can gain unauthorized access to admin panels, databases, or other sensitive areas of your website or server. This kind of attack is especially dangerous when weak or commonly used passwords are in place. Rate-limiting login attempts, enforcing strong password policies, and enabling two-factor authentication (2FA) are effective defenses.
2. Unauthorized root access:
- Root access refers to full administrative privileges on a server. If an attacker gains unauthorized root access, they can completely control the server, install or delete software, manipulate files, change configurations, and access or wipe out data.
- This often occurs through software vulnerabilities, unpatched systems, poor access controls, or leaked credentials. Once an attacker has root access, it’s incredibly difficult to detect or reverse the damage without full server audits or reinstallation. Securing SSH access, using firewalls, and regularly patching software are critical preventive measures.
3. Malware injections:
- Malware injection is a technique where malicious code is inserted into a website, application, or database with the goal of performing unauthorized actions. Common types of malware include trojans, ransomware, spyware, and crypto miners.
- Malware can be injected through insecure file uploads, outdated plugins, or SQL injection vulnerabilities. Once in place, it may steal sensitive data, redirect users to malicious sites, or compromise site functionality. Regular malware scanning, input sanitization, and file integrity monitoring are essential to prevent such attacks.
4. Data breaches:
- A data breach occurs when unauthorized individuals gain access to confidential or sensitive data, such as customer records, payment information, or internal documents. This can happen due to unencrypted data storage, weak access controls, social engineering attacks, or malware.
- Consequences of a data breach can be severe: legal penalties, loss of customer trust, reputational damage, and financial losses. Organizations must implement strong encryption, access control policies, regular audits, and incident response plans to mitigate the risk and impact of breaches.
5. DDoS attacks:
- In a DDoS attack, attackers use a network of compromised computers (a botnet) to flood a target server or website with overwhelming traffic. The goal is to exhaust system resources, such as CPU, RAM, or bandwidth, causing the service to slow down significantly or go offline entirely.
- DDoS attacks can last minutes, hours, or even days, disrupting business operations and denying service to legitimate users. Protection strategies include using firewalls, load balancers, rate-limiting, and third-party DDoS mitigation services like Cloudflare or AWS Shield.
Secure Your Server With ServerAvatar
ServerAvatar is a platform to simplify the hosting and management of servers and applications. It simplifies the process of deploying and managing PHP and Node.js based web applications on servers.
Manually applying all these hardening steps can be time-consuming and prone to errors, especially if you manage multiple servers or client projects.
That’s where ServerAvatar makes the difference. It automates and simplifies server management, so you can focus on running your applications instead of worrying about vulnerabilities and configurations.
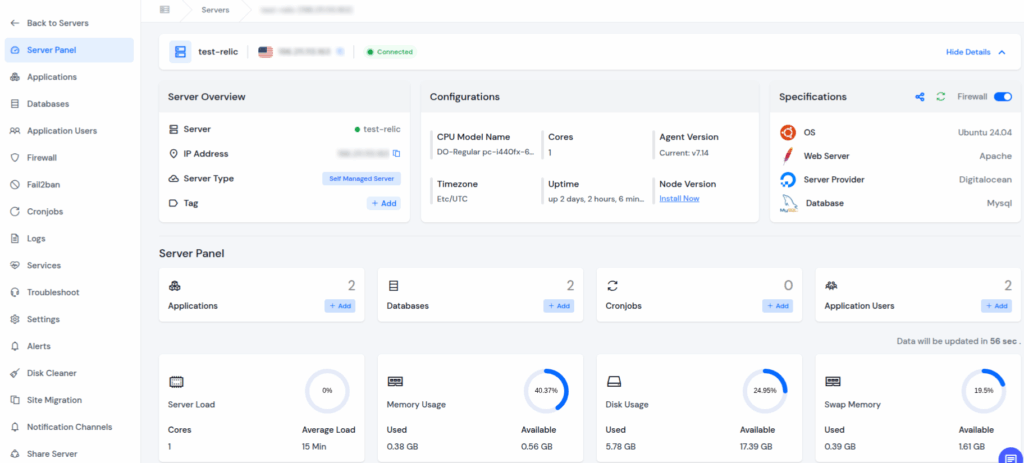
- Automated Security Configurations
- Automatically configures a secure firewall when you connect or deploy a server.
- Disables unnecessary services and sets strict firewall rules instantly.
- No need to manually edit configuration files or remember complex commands.
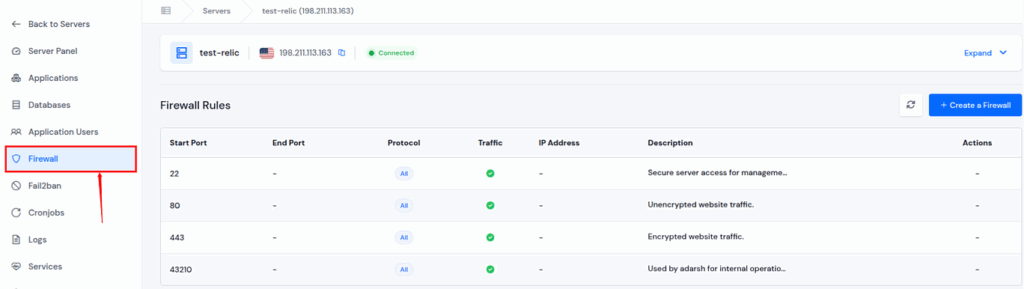
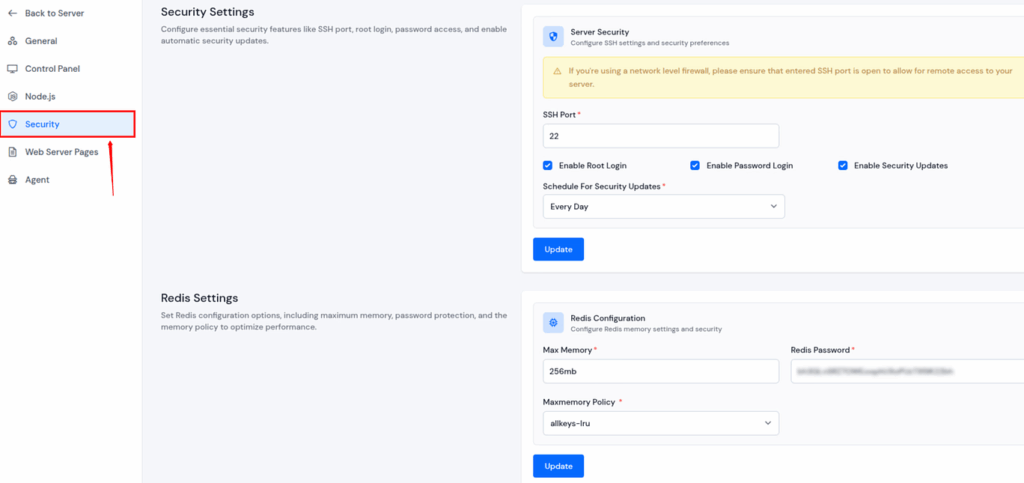
- Safe User Access and Authentication
- Create and manage non-root users securely.
- Disable password and root login in one click.
- Enable automatic security updates effortlessly.
- Change the default SSH Port easily.
- Ensures only authorized users can access your server while keeping hackers out.
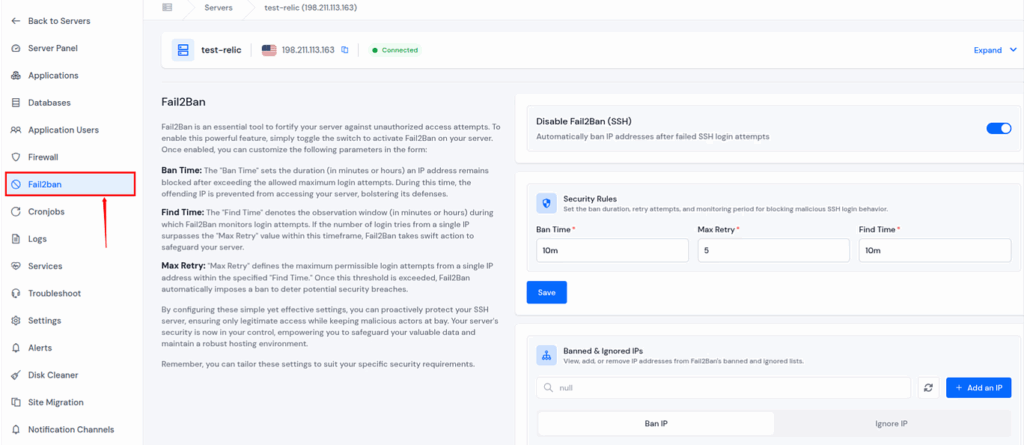
- Built-in Firewall and Fail2Ban Protection
- Enable or manage firewalls directly from the ServerAvatar dashboard.
- Open or close specific ports easily.
- Activate brute-force protection (Fail2Ban) to block malicious login attempts automatically.
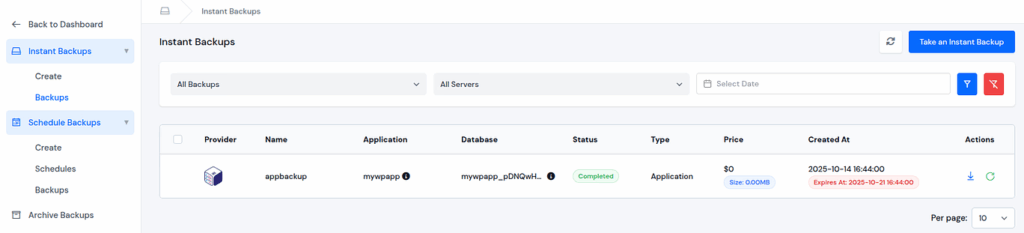
- Automated Backups and Restore
- Automate instant backups for all your applications and databases.
- Schedule backups as per your requirements.
- Restore data instantly in case of failure or attack, all with one click.

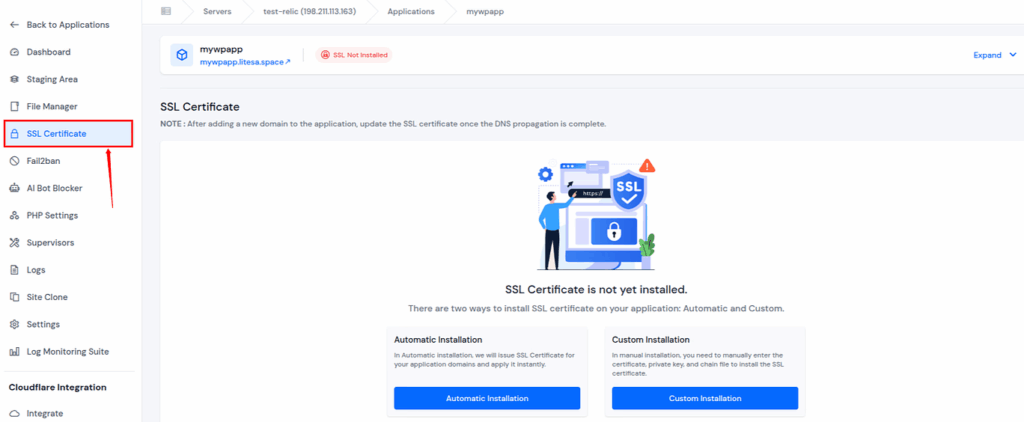
- SSL Management Made Simple
- One-click automatic and free SSL installation for all your websites.
- Automatic certificate renewal to ensure continuous HTTPS security.
- No manual configuration or command-line setup required.
- You can also install your own SSL Certificate if you want.
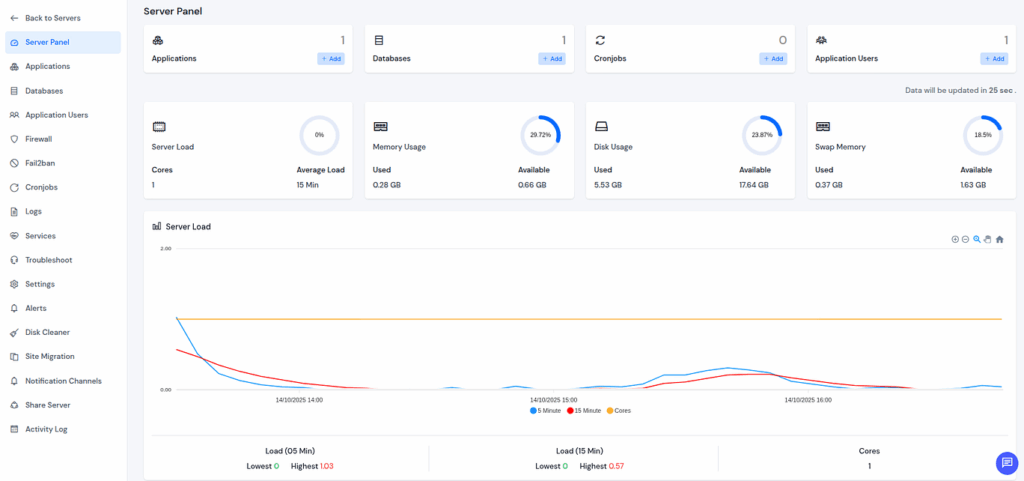
- Real-Time Log Monitoring and Alerts
- Built-in server health monitoring tracks CPU, memory, and disk usage.
- Receive alerts for unusual or potentially dangerous activity.
- Detect performance or security issues before they affect uptime.
- Save Time and Strengthen Security
- Manage, monitor, and secure all your servers from one unified dashboard.
- Eliminate the need for multiple third-party tools or manual scripts.
- Enjoy professional-grade protection for both managed and self-managed servers with just a few clicks.
In short, Server hardening doesn’t have to be difficult. With ServerAvatar, you can secure, monitor, and manage your Linux servers effortlessly, all from a clean, intuitive dashboard.
Keep your systems safe, your data protected, and your peace of mind intact, because with ServerAvatar, your server security is always in good hands.
FAQs
What is the main purpose of Linux server hardening?
It’s to reduce vulnerabilities and protect your server from attacks by applying best security practices.
How often should I update my Linux server?
At least weekly, but critical security updates should be applied immediately.
Do I need both a firewall and Fail2Ban?
Yes. The firewall filters unwanted traffic, and Fail2Ban blocks malicious IPs dynamically.
Does ServerAvatar support both managed and self-managed servers?
Yes, ServerAvatar secures and manages both managed and self-managed servers from one dashboard.
Can ServerAvatar help in hardening?
Absolutely. ServerAvatar automates many of these tasks, from log monitoring to backups and server access management.
Conclusion
Securing your Linux server isn’t just about following a checklist, it’s about building a strong, ongoing defense strategy. From updating your system to managing user access and configuring firewalls, every step plays a vital role in keeping your server safe.
However, doing all of this manually can be tedious, especially when you’re managing multiple servers or client projects. That’s where ServerAvatar steps in. With automated security configurations, built-in firewalls, real-time monitoring, and easy SSL management, it takes the complexity out of Linux server hardening.
In short, ServerAvatar helps you save time, eliminate risks, and stay one step ahead of cyber threats, so you can focus on what really matters: growing your applications and business with complete peace of mind.
