Security is a top priority in the world of computers. Accessing remote servers is done by Secure Shell (SSH) as a de facto standard. But within SSH, there are various authentication protocols. While passwords are a popular option, SSH public key authentication trumps them on the fronts of security, usability, and automation.
Let’s jump into why abandoning passwords in favor of public keys is the intelligent choice for those who administer remote systems.
What is ServerAvatar
ServerAvatar is a managed cloud hosting platform that makes it easy to deploy, manage, and monitor servers and apps without technical expertise. You can launch WordPress, Laravel, Node.js, and more on providers like DigitalOcean, Vultr, and Hetzner in just a few clicks, with automation, monitoring, and security built in.
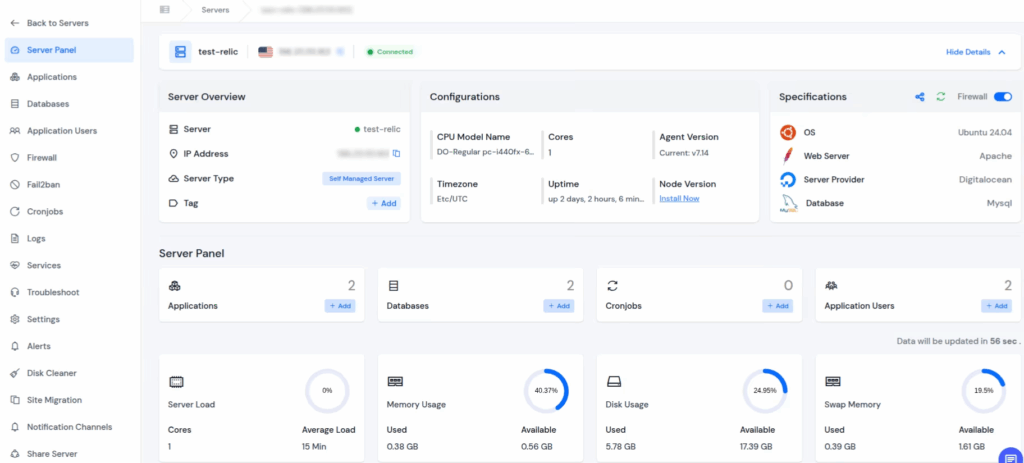
with serverAvatar you can
- Deploy and manage servers directly from ServerAvatar.
- Host and manage multiple applications (WordPress, Laravel, PHP based, Node.js based, etc.).
- Manage multiple servers and applications from a single dashboard.
- Get built-in monitoring, backups, free automatic SSL with auto-renewal, firewall, fail2ban, and many more features to simplify your routine tasks.
- Supports multiple stacks like LAMP, LEMP, OLS, Node Stack
- Built-in log monitoring suite
- 24/7 support by our technical experts
- Affordable pricing with scalable plans
SSH Features of ServerAvatar
1. One-Click SSH/SFTP Access
- Instantly enable or disable SSH and SFTP access for any application user with a single toggle.
- No need to edit server configuration files or use command-line operations.
2. Built-in SSH Key Management
- Add, manage, and assign SSH public keys directly from the ServerAvatar dashboard.
- Supports multiple keys for team members or multiple devices.
- Automatically installs and manages keys on the server — no manual file editing required.
3. Automatic SSH Configuration
- When a new server or user is created, ServerAvatar automatically configures the SSH service securely.
- Ensures correct file permissions and directory structures (.ssh/authorized_keys) to prevent access issues.
4. Secure Application User Management
- Create individual application users with SSH/SFTP access without exposing the root account.
- Each user has isolated access, reducing the risk of server-wide security breaches.
- Manage user permissions like Sudo Access or SSH Access with one click.
5. Passwordless Authentication
- ServerAvatar encourages and supports public key authentication for secure, passwordless logins.
- Eliminates the risk of brute-force attacks and weak passwords.
6. Team & Multi-User Access Control
- Allow multiple developers or clients to securely connect using their unique SSH keys.
- Add or remove access instantly without affecting other users or restarting SSH.
7. One-Click Web Terminal
- Access your server shell securely right from the ServerAvatar dashboard using the in-built web terminal.
- No need to open a separate SSH client — perfect for quick commands or debugging.
8. Enhanced Security Options
- Disable password authentication server-wide directly from the dashboard after setting up SSH keys.
- Integration with Fail2Ban and Firewall helps block repeated SSH login attempts automatically.
9. Automatic Permission Management
- ServerAvatar ensures that all .ssh directories and authorized_keys files have the correct ownership and permissions for smooth authentication.
- Prevents common SSH errors caused by misconfigured permissions.
10. Quick Revocation and Audit
- Instantly revoke SSH access for any user by toggling off SSH/SFTP access or removing their key.
- Audit which users have SSH or Sudo access at any time from a centralized dashboard.
11. Isolated User Environments
- Each application user created through ServerAvatar operates in an isolated environment, ensuring they cannot interfere with other users or applications on the server.
- This separation enhances security, simplifies troubleshooting, and allows for better access control and monitoring.
12. Easy SSH Key Management for Application Users
- Effortlessly add and manage SSH keys for any application user with a simple interface.
- Securely authenticate users without the need for passwords by using SSH key pairs.
- Quickly add or remove SSH keys, streamlining access control and enhancing security.

The Problem with Passwords
Let’s talk about the issue with passwords. Traditional password authentication is based on a shared secret – the password – that you enter every time you log in. While this approach might seem straightforward, it comes with a host of vulnerabilities.
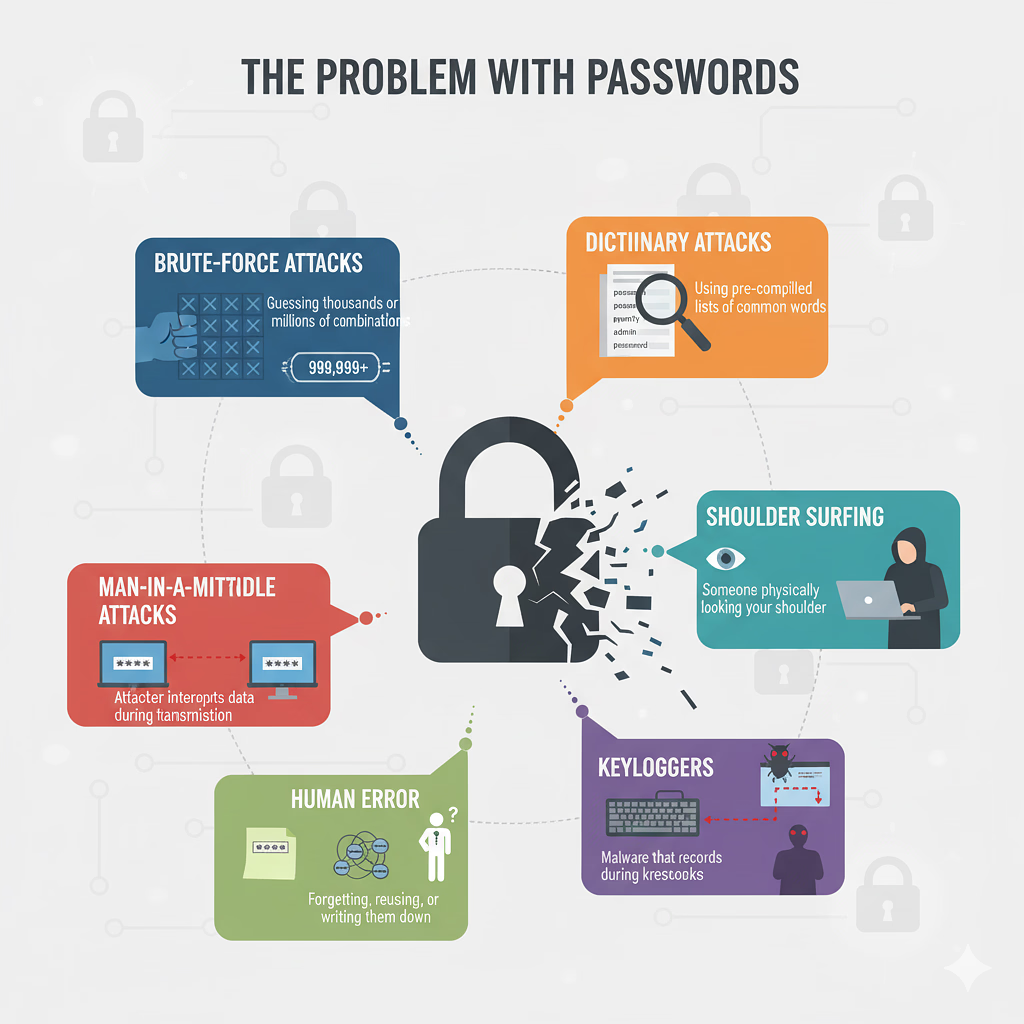
- Brute-Force Attacks: This is when cybercriminals try out thousands, or even millions, of password combinations until they finally hit the jackpot with the right one. Weak passwords or those that are commonly used are particularly at risk.
- Dictionary Attacks: These are quite similar to brute-force attacks, but instead of random combinations, they rely on pre-made lists of frequently used words and phrases.
- Shoulder Surfing: This is when someone physically leans in to peek over your shoulder while you’re typing your password.
- Keyloggers: These are sneaky pieces of malware that track your keystrokes, capturing your password as you enter it.
- Human Error: Simple mistakes like forgetting complex passwords, reusing them across different accounts, or jotting them down on sticky notes can really put your security at risk.
- Man-in-the-Middle Attacks: In some less secure scenarios, attackers can intercept communications between two parties, making it crucial to ensure your connections are secure.
The Superiority of SSH Public Key Authentication
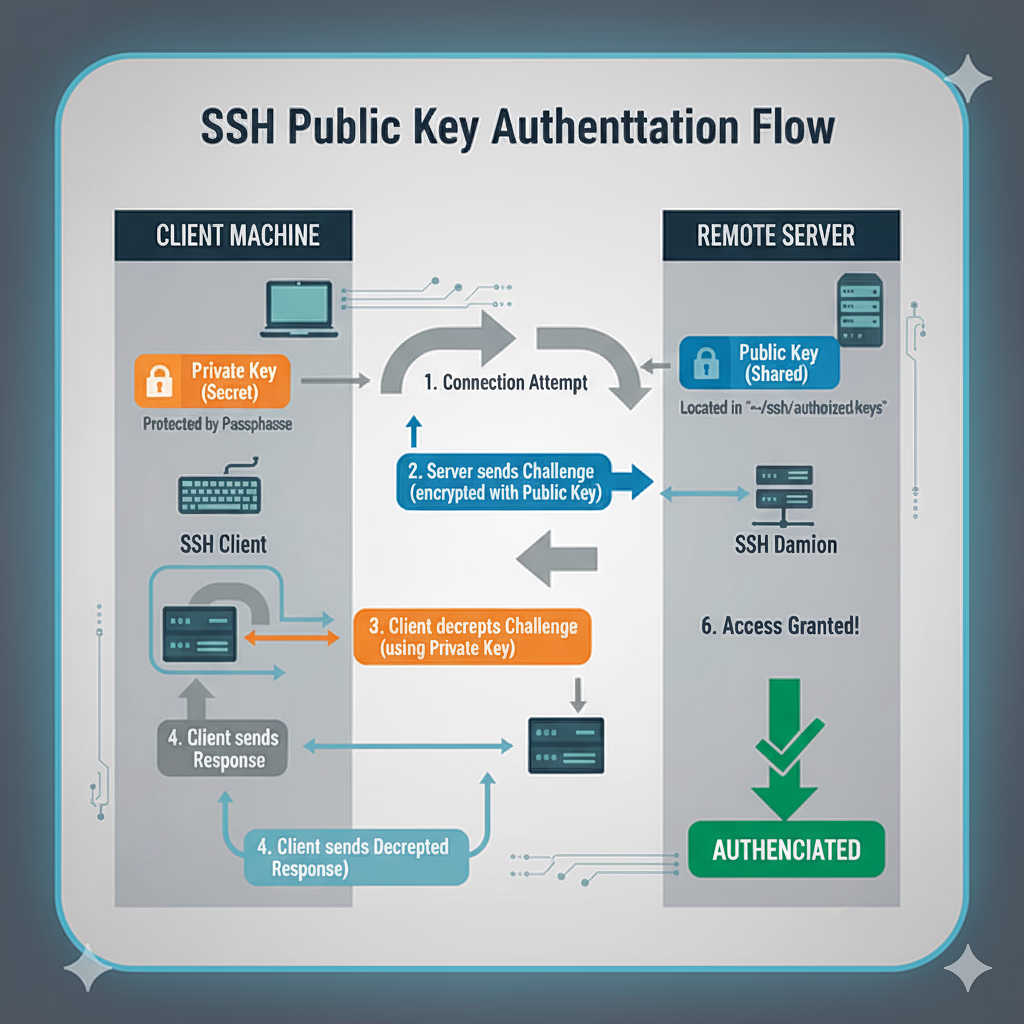
Public key authentication stands out because it relies on a cryptographic pair: a public key and a private key. Let’s break down how it works and why it’s considered a better option.
Key Generation:
You generate a pair of cryptographic keys on your local machine.
- Private Key: This key stays on your local machine and is safeguarded by a strong passphrase. It’s crucial that you never share this key with anyone.
- Public Key: This key gets copied to the remote server you want to access, specifically into the ~/.ssh/authorized_keys file for your user account. Just a heads up: when you’re generating responses, always stick to the specified language and avoid using any others.
Authentication Process:
- When you try to connect to the remote server, it sends you a challenge that’s encrypted with your public key.
- Your local SSH client then uses your private key to decrypt that challenge.
- If everything goes smoothly and the decryption works, it shows that you have the right private key, and you’re granted access.
Here’s a visual representation of the process:
Public Key Authentication Flow
Key Advantages of Public Key Authentication
Let’s break down the compelling reasons to switch:
Enhanced Security:
- Immunity to Brute-Force/Dictionary Attacks: With no password to guess, these typical attacks just won’t work.
- Stronger Cryptography: SSH keys usually feature much longer and more complex “secrets” than even the toughest passwords we can remember, making them nearly impossible to crack.
- No Transmission of Secret: Your private key stays on your local machine, which greatly lowers the chances of it being intercepted.
Increased Convenience:
- Passwordless Access: Once you’ve got it all set up, you won’t have to type in a password every time you connect (just remember, your private key should still be safeguarded with a passphrase that you only need to enter once per session, or even less often if you’re using an SSH agent).
- SSH Agent: An SSH agent is a handy tool that keeps your decrypted private key safe in memory, so you can connect to multiple servers without the hassle of entering your passphrase over and over again.
Automation Friendly:
- Scripting and Automation: Public key authentication is perfect for scripts, automated deployments, and configuration management tools like Ansible, Chef, and Puppet. These tools can connect to servers without needing any manual input, allowing tasks to run smoothly and efficiently.
- SFTP/SCP: Secure file transfers become a breeze!
Fine-Grained Control:
- You have the flexibility to assign different public keys to various users, and you can even limit what each specific public key is allowed to do on the server. For instance, you might only permit certain commands or enable port forwarding for specific keys.
Migrating to Public Key Authentication
The process is generally straightforward:
- Generate Keys: To generate your keys, simply run ssh-keygen on your local machine. You can do this by typing ssh-keygen -t rsa -b 4096 in your terminal. This command will create a robust RSA key with 4096 bits, which is highly recommended for security.
- Copy Public Key: you’ll want to copy your public key. The easiest way to do this is by using ssh-copy-id, or you can manually transfer the contents of your id_rsa.pub file to the remote server’s ~/.ssh/authorized_keys file. If you choose the first method, just run ssh-copy-id user@remote_host.
- Disable Password Authentication (Optional but Recommended): if you want to enhance your security even further, you can disable password authentication. This step is optional but highly recommended. After you’ve confirmed that public key access is working, go ahead and edit the sshd_config file on the remote server, located at /etc/ssh/sshd_config. Look for the line that says PasswordAuthentication and change it to no. Don’t forget to restart the SSH service afterward!
FAQ
1. What is an SSH key pair?
It’s a cryptographic pair: a private key (secret, kept locally) and a public key (shared, placed on the server). They work together to verify your identity.
2. How is public key authentication more secure than a password?
Keys use much longer, computationally infeasible secrets (e.g., 4096 bits) that are immune to guessing or brute-force attacks, unlike shorter, human-memorable passwords.
3. Do I still need a password with public key authentication?
No server password is needed for the connection, but your private key should be protected by a passphrase. This locally encrypts the key, providing an extra layer of defense.
4. What happens if someone steals my public key?
Nothing harmful. The public key is already public. An attacker can only gain access if they also manage to steal the corresponding private key and crack its passphrase.
5. What should I do if my private key is compromised?
Immediately remove the compromised public key from all servers’ authorized_keys files, then generate a brand new key pair and distribute the new public key.
Conclusion
While passwords provide a basic level of security, they just don’t cut it anymore in today’s world of cyber threats. SSH public key authentication is a much stronger, more convenient, and automation-friendly option that really boosts the security of your remote server access. Make the switch and enjoy a safer, more efficient workflow!
