When you connect to the internet or a private network, a lot of complex routing and communication happens silently in the background. One of the key technologies that makes this smooth and efficient is subnetting. Whether you manage servers, work with cloud infrastructure, or simply want to understand how networks stay organized, subnetting is a concept worth knowing.
In this guide, we’ll break down what subnetting is, how it works, and why it plays such an important role in modern networking, especially for system administrators, DevOps engineers, and businesses running applications at scale.
What Is Subnetting?
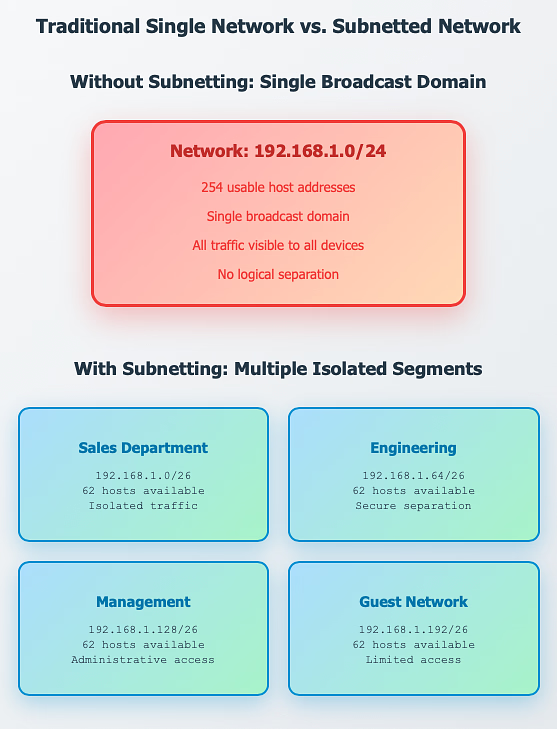
Subnetting is the process of dividing a larger IP network into multiple smaller networks called subnets. Instead of placing every device on one giant network, subnetting organizes devices into different groups, similar to dividing a large city into smaller neighborhoods.
Each subnet gets:
- Its own IP range
- Its own broadcast domain
- Its own security rules and access controls
At the technical level, subnetting is done by extending the network portion of an IP address. This is achieved by borrowing bits from the host portion and using them to create new network identifiers.
For example:
- A /24 network can be split into four /26 subnets
- Each of those subnets gets fewer host addresses but gains independence and structure
Subnetting isn’t just a math exercise; it’s a foundational tool for designing networks that are easier to scale, protect, and troubleshoot.
Why Subnetting Matters
Subnetting brings several major benefits that directly affect how well a network performs and how secure it is.
1. Improved Network Performance
Without subnetting, all devices share the same broadcast domain. This means every broadcast message, like ARP requests or DHCP discovery packets, reaches every device, even if it’s irrelevant.
As a network grows, this unnecessary traffic creates:
- Congestion
- Slow response times
- Higher load on devices
Subnetting contains this noise. Each subnet becomes its own broadcast domain, meaning broadcasts only reach devices within the same group. The result is noticeably faster, more efficient communication.
2. Stronger Security Through Segmentation
If all devices live on the same network, they can all communicate freely. That’s risky.
Subnetting allows you to isolate:
- Guest networks
- Servers
- Finance departments
- IoT devices
- Development/testing environments
Segmentation prevents sensitive systems from being exposed to general users and limits the impact of malware or unauthorized access. Even if an attacker gains access to one subnet, they cannot instantly reach all others.
3. Better IP Address Utilization
IPv4 addresses are limited and often assigned in large blocks. Without subnetting, organizations either waste huge chunks of IP space or overcrowd the network.
Subnetting allows you to:
- Right-size subnets based on device count
- Avoid wasting unused addresses
- Support future growth without redesigning the network
This efficiency is crucial in modern networks, especially when using private IP ranges that must be carefully planned.
4. Easier Troubleshooting and Network Management
Subnetting makes networks predictable and structured.
When a problem occurs, like a faulty device, configuration issue, or broadcast storm, you can narrow it down to a specific subnet rather than searching the entire network.
This leads to:
- Faster issue resolution
- Simpler monitoring
- Clearer documentation
- Easier maintenance
Subnetting gives administrators better visibility and control.
5. Logical Organization That Mirrors the Business
Networks usually reflect how a company works. With subnetting, you can assign:
- One subnet per department
- One subnet per building or floor
- One subnet per device category
This logical structure keeps everything clean, easy to understand, and aligned with organizational needs.
How Subnetting Works
The internet relies on IP addresses, which look something like:
192.168.1.100Each IP address has two main parts:
- Network ID: Identifies the network
- Host ID: Identifies the device within that network
Subnetting changes how many bits are used for the network part and how many for the hosts.
A subnet mask (like 255.255.255.0) defines this boundary.
Example:
- Network: 192.168.1.0/24
- Subnet mask: 255.255.255.0
- This allows 256 total IPs, with 254 usable for devices.
With subnetting, you could split this into smaller pieces:
- 192.168.1.0/26
- 192.168.1.64/26
- 192.168.1.128/26
- 192.168.1.192/26
Each of these now allows 64 IPs, giving you more control over traffic and allocation.
Deep Dive: IP Addresses and Subnet Masks
Understanding IP Addresses
- Every IPv4 address contains 32 bits.
- These 32 bits are shown in dotted decimal format (e.g., 192.168.1.10).
- The address is divided into 4 octets, each containing 8 bits.
- Each octet can range from 0 to 255.
- IP addresses are split into:
- Network portion
- Host portion
Role of the Subnet Mask
A subnet mask defines where the network ends and the host part begins.
Example:
- Subnet mask 255.255.255.0 = /24 in CIDR.
- This means 24 bits for the network and 8 bits for hosts.
Subnet masks are essential for:
- Dividing networks
- Routing traffic
- Organizing devices properly
Binary Representation: The Foundation of Subnetting
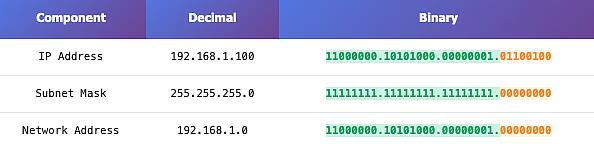
- Subnetting relies on understanding IP addresses in binary form.
- Both the IP address and subnet mask are converted to binary.
- The number of 1s in the subnet mask identifies the network portion.
- The number of 0s identifies the host portion.
- Binary helps determine:
- Total hosts
- Subnet ranges
- Network calculations
Understanding CIDR Notation
- CIDR stands for Classless Inter-Domain Routing.
- It uses a shorthand format like: 192.168.1.0/24.
- The number after / indicates:
- How many bits are used for the network part.
- Remaining bits determine the number of host addresses.
- CIDR is more flexible than traditional class-based addressing.
Formula to Calculate Number of IPs
Number of IP addresses = 2^(32 - prefix length)- 32 represents the total bits in an IPv4 address.
- Prefix length is the number after the slash in the CIDR notation.
Example Calculations
- For a CIDR block 192.168.1.0/24:
- Prefix length = 24
- Number of IP addresses = 2^(32 – 24) = 2^8 = 256 IPs
- For 10.0.0.0/16:
- Prefix length = 16
- Number of IP addresses = 2^(32 – 16) = 2^16 = 65,536 IPs
- For 172.16.0.0/20:
- Prefix length = 20
- Number of IP addresses = 2^(32 – 20) = 2^12 = 4,096 IPs

CIDR Impact
- Increasing the prefix (e.g., from /24 to /25):
- Halves available host addresses.
- Doubles the number of subnets.
- /30 networks
- Provide only 2 usable host addresses.
- Commonly used for point-to-point links between routers.
- /24 networks
- Typically used for departmental LANs or small to medium-sized networks.
Subnetting in the Real World
1. Cloud Infrastructure
Platforms like AWS, Google Cloud, and DigitalOcean let you divide your VPC into subnets:
- Public subnets for internet-facing apps
- Private subnets for databases
- Isolated subnets for internal services
This structure is only possible because of subnetting.
2. Server Management
Modern server management platforms like ServerAvatar rely on clean network segmentation to ensure smooth server operations.
Subnetting helps ServerAvatar manage:
- Application isolation
- Load balancers
- Failover configuration (Contact Technical Support Team for configure failover they are available 24/7 to assist you)
- SSL configurations
- Multiple environments (production, staging, testing)
- Secure inter-service communication
With well-designed subnets:
- Traffic flows more efficiently
- Firewalls become easier to manage
- Security zones remain isolated
- High-availability setups become more reliable
ServerAvatar takes care of server provisioning, isolation, firewalls, and routing, but behind the scenes, it benefits greatly from clean subnet planning.
3. Office Networks
Companies use subnetting to separate:
- Admin department
- HR
- Finance
- Guest networks
- Surveillance systems
This ensures better privacy and reduces internal network noise.
4. Data Centers
Subnetting is crucial for:
- Cluster organization
- High-availability setups
- Storage networks
- VLAN segmentation
Key Subnetting Terms You Should Know
1. IP Address
A unique number identifying a device on the network.
IPv4 example: 192.168.10.5
2. Subnet Mask
A pattern defining which part of the IP is the network and which part is the host.
Example: 255.255.255.0
3. CIDR Notation
A shorthand version of subnet masks.
Example: /24
4. Network Address
The first address in a subnet.
Example: 192.168.1.0
5. Broadcast Address
The last address in a subnet.
Example: 192.168.1.255
6. Usable Host Range
All IPs between the network and broadcast addresses.
Step-by-Step Subnetting Process: Mastering the Calculations
Learning to subnet effectively requires understanding both the mathematical principles and the practical application. Let’s work through the complete process with detailed examples.
The Five-Step Subnetting Method:
Step 1: Determine Requirements
Before starting any calculations, clearly define your requirements:
- How many subnets do you need?
- How many hosts per subnet?
- What is your starting network address?
- Do you need room for future growth?
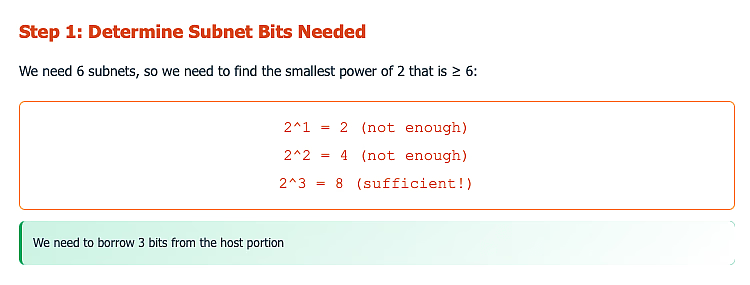
Step 2: Calculate Required Subnet Bits
- Use the formula: 2^n ≥ number of required subnets
- Where n = number of bits to borrow from the host portion
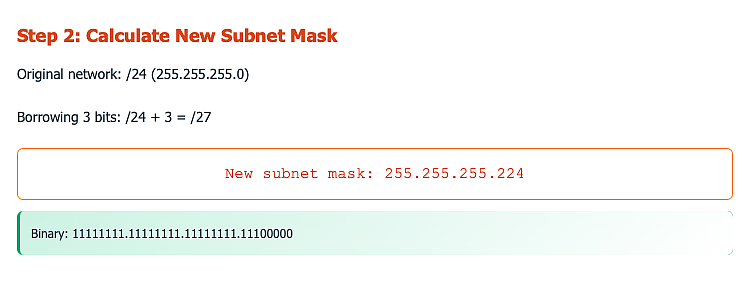
Step 3 : Determine New Subnet Mask
- Add bits to the original subnet mask that are borrowed
- For example: Original bits is 24 and borrowed bits is 2
- Original /24 + 2 borrowed bits = /26
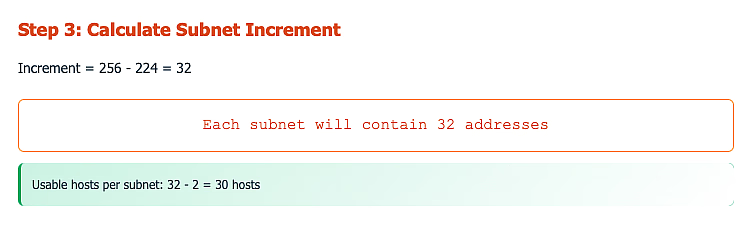
Step 4 : Calculate Subnet Increment
- Subtract the new subnet mask value from 256
- This gives you the address increment between subnets
Step 5: List All Subnet Ranges
- Starting from the network address, list each subnet using the calculated increment
Detailed Example: Subnetting 192.168.100.0/24
Requirement: Create 6 subnets for different departments
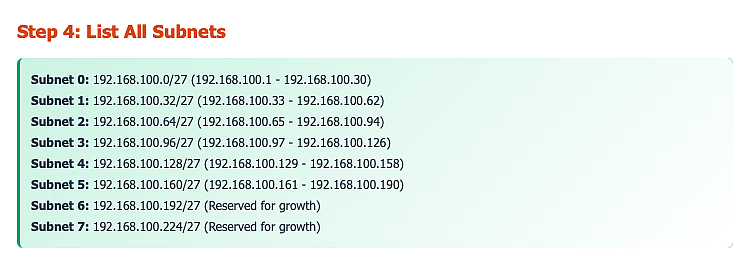

Advanced Technique: Variable Length Subnet Masking (VLSM)
What Is VLSM?
VLSM stands for Variable Length Subnet Masking. It allows you to create subnets of different sizes within the same network. Unlike fixed-length subnetting, VLSM allocates IP addresses based on actual needs, reducing waste. It is widely used in modern, scalable, and efficient network designs.
Why VLSM Is Important
Traditional subnetting assigns the same subnet size to every segment, causing unnecessary IP wastage.
VLSM enables more precise allocation, ensuring different departments or networks get subnets tailored to their device count.
Helps achieve:
- Better IP utilization
- More organized addressing
- Greater flexibility in design
VLSM in Practice: Optimizing Address Allocation
Useful when network segments vary greatly in size. Instead of giving a large subnet to every department, VLSM assigns:
- Large subnets to high-demand areas
- Small subnets to low-demand areas
This ensures every department gets “just enough” IPs, nothing wasted, nothing lacking.
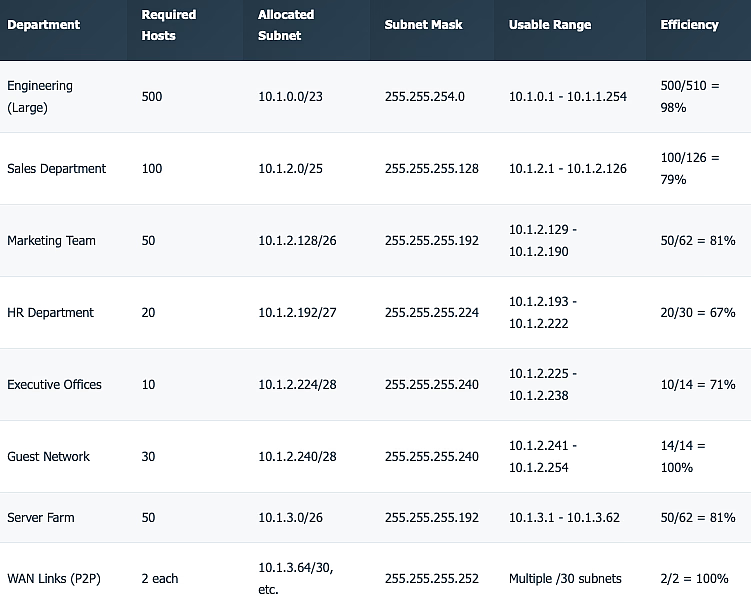
Example Scenario: Medium Enterprise
- Starting network: 10.1.0.0/16
- Total usable addresses: 65,534
- Company departments may include:
- HR (50 devices)
- Finance (120 devices)
- IT (500 devices)
- Guest WiFi (200 devices)
- Security systems (30 devices)
- VLSM allows assigning each department a suitable subnet size based on the number of required hosts.
VLSM Design Principles
- Start with the largest requirements
- Assign subnets to the biggest groups first to prevent address fragmentation.
- Work systematically
- Move through the IP address block in order to avoid gaps and overlaps.
- Plan for future growth
- Allocate extra space for departments that may expand.
- Use hierarchical addressing
- Group related subnets together for easier routing and management.
- Document everything
- VLSM networks can get complex; maintaining clear documentation prevents confusion and errors.
VLSM Step-by-Step Calculation Strategy
1. List Requirements in Descending Order: Always start with the largest subnet requirements and work your way down. This prevents address space fragmentation.
2. Calculate Subnet Sizes: For each requirement, determine the smallest subnet that can accommodate the needed number of hosts plus growth.
3. Allocate Sequentially: Assign subnets in order through your address space, ensuring no overlap.
Example VLSM Allocation Process
Starting with 172.16.0.0/16 (65,534 hosts available) Requirements (sorted by size):
- Engineering: 1000 hosts → Need /22 (1022 hosts) → 172.16.0.0/22
- Sales: 400 hosts → Need /23 (510 hosts) → 172.16.4.0/23
- Marketing: 200 hosts → Need /24 (254 hosts) → 172.16.6.0/24
- HR: 50 hosts → Need /26 (62 hosts) → 172.16.7.0/26
- IT: 25 hosts → Need /27 (30 hosts) → 172.16.7.64/27
- Executives: 10 hosts → Need /28 (14 hosts) → 172.16.7.96/28
Remaining space: 172.16.7.112/28 through 172.16.255.0/24
Available for future growth: 65,000+ addresses
Traditional Flat Network Vs. Well-Designed Subnetting
| Aspect | Traditional Flat Network | Well-Designed Subnetting |
| Route Summarization | No summarization possible; large routing tables | Hierarchical addressing enables efficient summarization |
| Failure Isolation | Network issues affect the entire organization | Problems contained within affected subnets |
| Security Policy Implementation | Host-based security only; complex ACLs | Subnet-based policies; clear security boundaries |
| Performance Monitoring | Difficult to identify traffic patterns | Clear visibility into departmental network usage |
| Change Management | Changes affect entire network | Gradual rollouts possible; limited impact |
| Troubleshooting | Changes affect the entire network | Issues isolated to specific network segments |
| Bandwidth Management | Difficult to implement per-department policies | QoS and traffic shaping per subnet |
Common Subnetting Mistakes and How to Avoid Them
Even experienced network professionals can fall into common subnetting traps. Understanding these pitfalls and how to avoid them is crucial for successful network implementations.
1. Overlapping Subnet Ranges
- Problem: Accidentally creating subnets that share IP addresses
- Example: 192.168.1.0/25 and 192.168.1.64/26 overlap
- Solution: Use systematic allocation methods; always verify calculations; use IPAM tools
2. Inadequate Growth Planning
- Problem: Creating subnets too small for future expansion
- Example: /28 subnet for department expected to double in size
- Solution: Plan for 2-3x current requirements; reserve contiguous space for expansion
3. Poor Hierarchical Design
- Problem: Random subnet allocation preventing route summarization
- Example: Department subnets scattered across address space
- Solution: Use hierarchical addressing; group related subnets together
4. Inadequate Documentation
- Problem: Lost track of subnet allocations and purposes
- Example: Unknown subnets discovered during network audits
- Solution: Maintain comprehensive IPAM records; document all allocations
5. Ignoring Security Implications
- Problem: Mixing security zones within subnets
- Example: Servers and workstations in same subnet
- Solution: Align subnet design with security architecture; separate trust zones
6. Broadcast Domain Oversights
- Problem: Creating subnets too large, causing performance issues
- Example: 1000+ devices in single /22 subnet
- Solution: Limit broadcast domains; consider performance implications
FAQs
1. What is the main purpose of subnetting?
Subnetting improves performance, enhances security, and simplifies troubleshooting by isolating traffic within specific subnets.
2. How does subnetting improve network performance?
By reducing the size of broadcast domains, subnetting prevents unnecessary traffic from reaching every device. This reduces congestion and helps the network operate more efficiently.
3. What is a subnet mask, and why is it important?
A subnet mask defines how much of an IP address belongs to the network portion and how much is used for hosts. This boundary is essential for routing and determining subnet size.
4. What is CIDR notation?
CIDR (Classless Inter-Domain Routing) represents IP addresses using a prefix format, such as /24 or /16. The number indicates how many bits are used for the network, making subnetting easier and more flexible.
5. Why is VLSM better than fixed-length subnetting?
VLSM allows different subnets to have different sizes. This ensures IP addresses are allocated efficiently, large subnets for departments with many devices and smaller subnets for areas that need fewer addresses.
Conclusion
Subnetting is more than just a networking concept, it’s a critical foundation that keeps modern systems fast, scalable, and secure. Whether you’re working with cloud platforms, managing servers, or designing enterprise networks, subnetting helps you build structured, efficient environments.
Tools like ServerAvatar make server and application management incredibly simple, but understanding subnetting gives you deeper control over routing, security, and performance. As networks grow, mastering CIDR, subnet masks, and VLSM becomes essential for building future-ready infrastructure.
Stop Wasting Time on Servers. Start Building Instead.
You didn’t start your project to babysit servers. Let ServerAvatar handle deployment, monitoring, and backups — so you can focus on growth.
Deploy WordPress, Laravel, N8N, and more in minutes. No DevOps required. No command line. No stress.
Trusted by 10,000+ developers and growing.
