Security in modern DevOps environments is no longer about building strong walls—it’s about continuously verifying trust. As DevOps accelerates software delivery, traditional security methods can’t keep up. That’s where Zero Trust steps in, ensuring every access request is authenticated, authorized, and encrypted.
Zero Trust has become a crucial part of DevOps workflows because it blends security and automation seamlessly, without slowing down deployments.
Zero Trust in DevOps means verifying every access request, no implicit trust. It secures CI/CD pipelines, automation tools, and cloud resources without slowing down deployment.
What Is Zero Trust?
Zero Trust is not a product, it’s a philosophy. The concept is simple: “Never trust, always verify.”
Unlike old security methods that assume internal traffic is safe, Zero Trust assumes every request could be a threat. It validates each action based on identity, device health, and behavior before granting access.
For example, if a developer logs into a server or pushes code to a repository, the system reauthenticates the session, ensuring no compromised credentials are used.
Why Traditional Security Models Fail in DevOps
In the past, companies used perimeter-based security, like a firewall around a castle. Once inside, users were trusted completely. However, with cloud computing, remote work, and APIs, that model doesn’t hold up anymore.
Attackers can easily exploit weak internal links, misconfigured servers, or compromised credentials.
Zero Trust eliminates this flaw by treating every user, system, and device as untrusted until proven otherwise.
Why Zero Trust Is Crucial for DevOps
DevOps thrives on speed and automation, but these same qualities make it vulnerable. Frequent deployments, open APIs, and shared repositories increase exposure to risks.
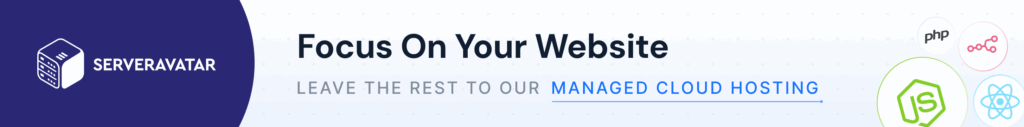
Key Reasons DevOps Needs Zero Trust
- Dynamic infrastructure: Containers, microservices, and cloud resources change constantly.
- Multiple access points: Developers, automation tools, and third-party APIs all interact.
- Continuous integration and delivery (CI/CD): Without strong identity control, one breach can compromise the entire pipeline.
By implementing Zero Trust, DevOps teams can maintain velocity without sacrificing security.
Core Principles of Zero Trust Architecture
- Identity Verification – Authenticate every user and device using IAM and MFA before granting access.
- Least Privilege Access – Give only the permissions needed to perform a task, nothing more.
- Micro-Segmentation – Divide infrastructure into small zones to contain breaches.
- Continuous Monitoring – Detect anomalies in real time using automated alerts and logging tools.
These principles ensure that even if one layer is compromised, the rest remain protected.
How Zero Trust Aligns with DevOps Culture
Zero Trust fits perfectly with DevSecOps, where development, security, and operations work together.
Instead of seeing security as an obstacle, Zero Trust turns it into an automated guardrail built into your workflow.
Security policies can be defined as code, automatically verified during builds and deployments. That means developers don’t have to manually handle security—it’s just part of the pipeline.
Key Components of Zero Trust in DevOps
- IAM (Identity and Access Management): Controls who accesses what.
- MFA (Multi-Factor Authentication): Adds layers of verification.
- RBAC (Role-Based Access Control): Limits permissions based on user roles.
- Secrets Management: Protects sensitive credentials using tools like HashiCorp Vault or AWS Secrets Manager.
- Network Segmentation: Divides infrastructure for better isolation and control.
Challenges of Adopting Zero Trust
While Zero Trust offers major benefits, implementation isn’t without hurdles:
- Integration Complexity: Coordinating between multiple tools and systems.
- Developer Resistance: Some may see it as slowing down work.
- Cost: Upgrading infrastructure and licenses can be expensive.
- Visibility Gaps: Legacy systems might not support Zero Trust frameworks easily.
Overcoming these challenges requires planning, automation, and collaboration between DevOps and security teams.
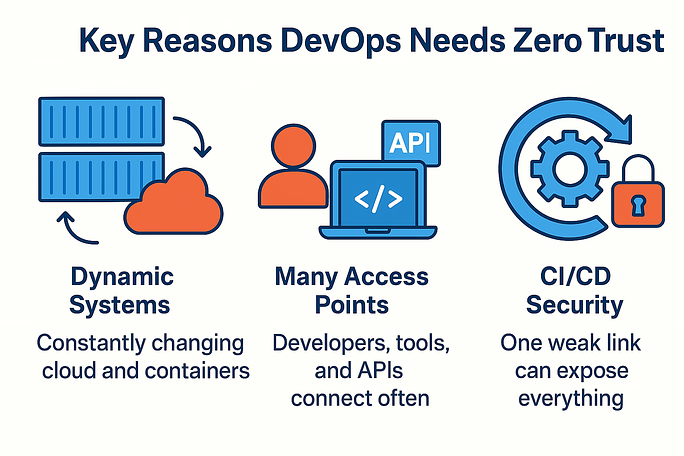
Step-by-Step Guide to Implement Zero Trust in DevOps
Step 1: Identify Critical Assets
Start by listing what you must protect, repositories, databases, CI/CD systems, or servers.
Step 2: Implement Identity-Based Access
Use IAM and MFA to enforce strict access policies. Only verified users can perform specific actions.
Step 3: Secure Pipelines and Automation Tools
Limit what your CI/CD tools (like Jenkins or GitHub Actions) can access.
Step 4: Monitor and Respond to Threats
Deploy SIEM tools like Splunk or Datadog to detect unusual activities.
Step 5: Audit and Continuously Improve
Regularly review logs, rotate credentials, and tighten weak configurations.
Tools Supporting Zero Trust in DevOps
Some powerful tools to help build and maintain a Zero Trust environment:
- Okta / Azure AD: Manage user identities and policies.
- HashiCorp Vault: Securely store and rotate secrets.
- AWS IAM: Enforce permissions across cloud services.
- Splunk / ELK Stack: Monitor system behavior and detect threats.
- ServerAvatar: Manage server security with built-in monitoring and role-based access.

Zero Trust in Cloud and Hybrid Infrastructures
In cloud computing, Zero Trust ensures security remains consistent—no matter where workloads run.
Whether you’re on AWS, Google Cloud, or Azure, the model verifies every connection.
In hybrid setups, Zero Trust helps unify security across on-premises and cloud environments, ensuring seamless protection across systems.
AI and Automation in Zero Trust
AI brings predictive power to Zero Trust. It analyzes user behavior, detects unusual logins, and blocks threats automatically.
For example:
- If a developer suddenly accesses production data from a new country, AI flags or blocks it.
- Automated systems can revoke access instantly if an anomaly is detected.
AI ensures that Zero Trust remains dynamic and proactive, not just reactive.
Server Management and Zero Trust
Server management platforms like ServerAvatar help teams implement Zero Trust practically by:
- Automating role-based access control (RBAC)
- Managing and rotating credentials
- Monitoring server activity and performance logs
- Enforcing security patches automatically
This allows DevOps teams to maintain compliance and visibility with minimal manual work.
FAQs
What is the core idea behind Zero Trust?
The principle of “never trust, always verify”—every access request must be authenticated, no matter its origin.
Can Zero Trust slow down DevOps pipelines?
If automated properly, Zero Trust enhances speed by removing manual checks and ensuring secure automation.
How can AI improve Zero Trust?
AI detects anomalies, predicts risks, and automates responses for faster and smarter security enforcement.
Is Zero Trust only for large companies?
No, even small teams can benefit from Zero Trust by securing critical assets with IAM, MFA, and monitoring tools.
What’s the first step to adopt Zero Trust in DevOps?
Start by identifying your sensitive assets and implementing identity-based access controls.
Conclusion
Zero Trust isn’t about slowing down—it’s about securing your growth.
In DevOps environments where speed is everything, Zero Trust creates a balance between agility and safety.
By verifying every access, minimizing privileges, and monitoring continuously, your systems stay one step ahead of potential breaches.
Embrace Zero Trust today to build a safer, smarter, and more reliable DevOps culture. Zero Trust isn’t just a framework, it’s the foundation for secure, scalable, and automated DevOps. Start implementing it today with ServerAvatar and safeguard every deployment.
Stop Wasting Time on Servers. Start Building Instead.
You didn’t start your project to babysit servers. Let ServerAvatar handle deployment, monitoring, and backups — so you can focus on growth.
Deploy WordPress, Laravel, N8N, and more in minutes. No DevOps required. No command line. No stress.
Trusted by 10,000+ developers and growing.
